The IoT is not the only range of devices connected to the Internet, but it is also a very complex, rapidly growing technology. To understand and analyze various risk factors, proper security solutions must be incorporated to protect the IoT devices. The use of IoT security tools helps organizations to significantly limit security vulnerabilities, thereby protecting the IoT devices and networks from different kinds of attacks.
SeaCat.io
Source: https://www.teskalabs.com
SeaCat.io is a security-first SaaS technology to operate IoT products in a reliable, scalable, and secure manner. It provides protection to end-users, businesses, and data. Security professionals use SeaCat.io to manage connected products from a central place, access remote devices using various tools, monitor connected devices and automate updates to fix bugs, protect users with authorized cryptography and comply with regulations, ensure devices are malware-free and prevent hackers from controlling them and making them part of a botnet, etc.
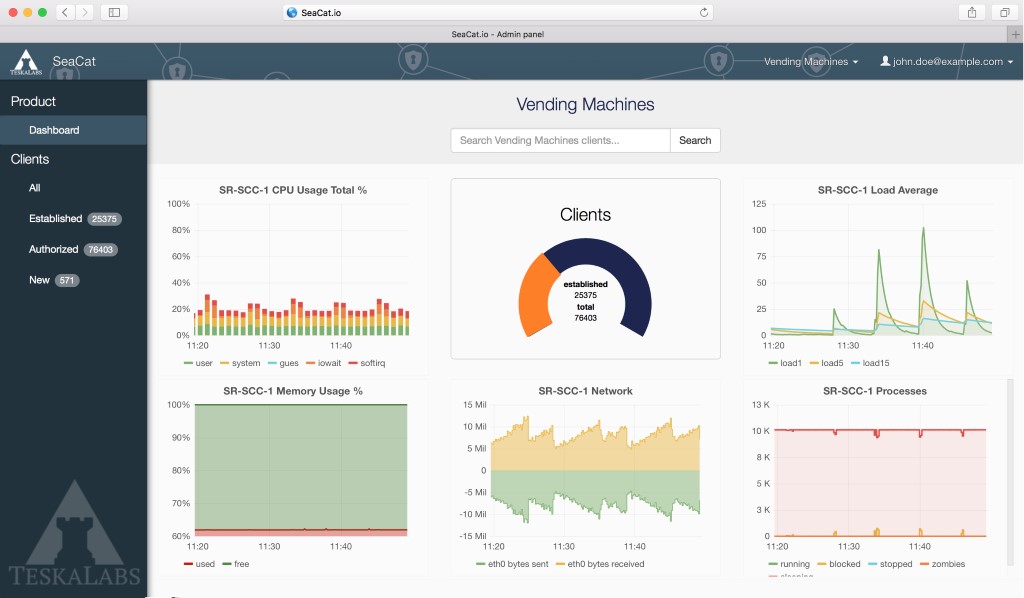
Figure 10.13: Screenshot of SeaCat.io
Listed below are some of the additional IoT security tools and solutions:
DigiCert IoT Device Manager (https://www.digicert.com)
FortiNAC (https://www.fortinet.com)
darktrace (https://www.darktrace.com)
Symantec Critical System Protection (https://www.symantec.com)
Cisco IoT Threat Defense (https://www.cisco.com)
Many IoT devices, such as security cameras, host a website for controlling or configuring the cameras from a remote location. These websites mostly implement the insecure HTTP protocol instead of HTTPS, and are vulnerable to various attacks. If the cameras are using default factory credentials, an attacker can easily intercept all the traffic flowing between the camera and web application and further gain access to the camera itself. Attackers can use tools such as Wireshark to intercept such traffic and decrypt the Wi-Fi key of the target network.
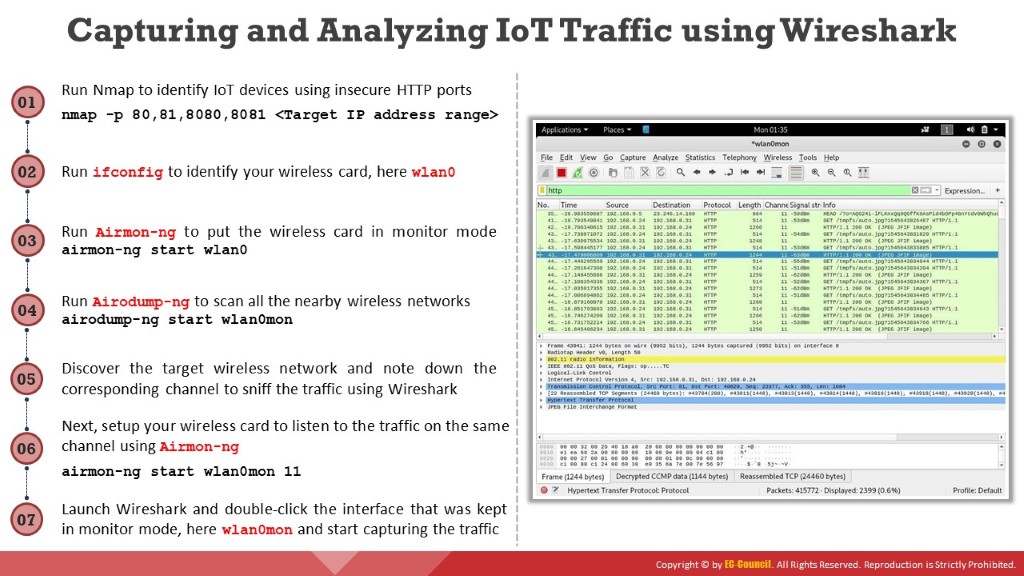
Steps used by attackers to sniff wireless traffic of a web camera:
Run Nmap to identify IoT devices using insecure HTTP ports for transmitting data:
nmap -p 80,81,8080,8081 <Target IP address range>
Now, set up your wireless card in monitor mode and identify the channel used by the target router for broadcasting. For this, run ifconfig to identify your wireless card, here: wlan0
Run Airmon-ng to put the wireless card in monitor mode:
airmon-ng start wlan0
Next, run Airodump-ng to scan all the nearby wireless networks:
airodump-ng start wlan0mon
Now, discover the target wireless network and note down the corresponding channel to sniff the traffic using Wireshark
Next, set up your wireless card to listen to the traffic on the same channel. For example, if the target network’s channel is 11, run Airmon-ng to set your wireless card listening on channel 11:
airmon-ng start wlan0mon 11
Launch Wireshark and double-click the interface that was kept in monitor mode, here wlan0mon, and start capturing the traffic
After capturing the traffic, attackers can analyze and decrypt the WEP and WPA keys using Wireshark and can hack the target IoT device to steal sensitive information.
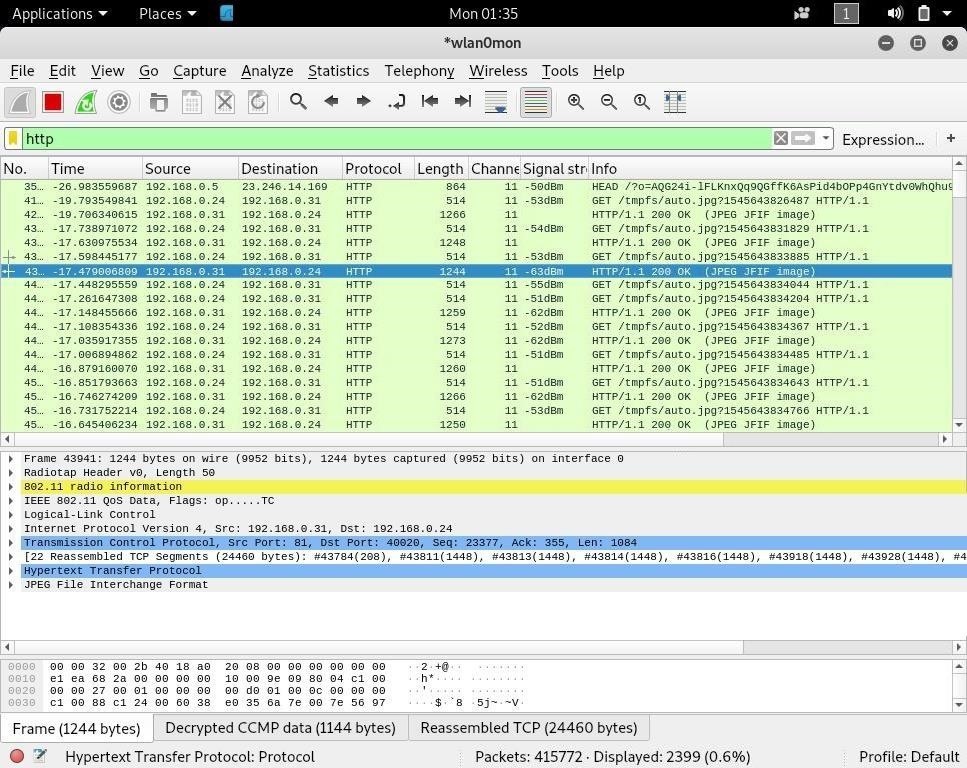
Figure 10.11: Screenshot of Wireshark
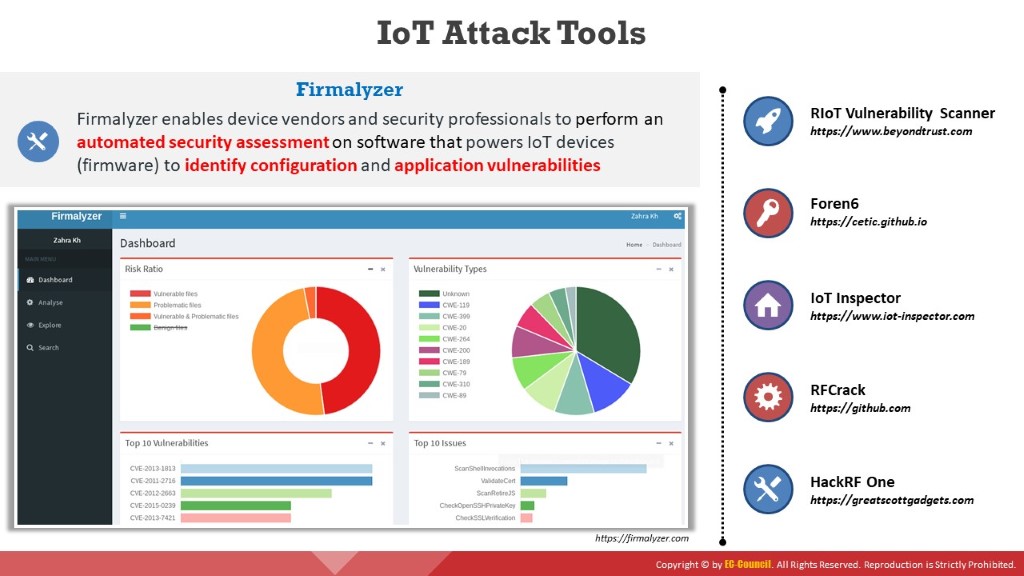
Listed below are some of the IoT hacking tools used by attackers to exploit target IoT devices and networks to perform various attacks such as DDoS, jamming, and BlueBorne attacks.
Firmalyzer
Source: https://firmalyzer.com
Firmalyzer enables device vendors and security professionals to perform an automated security assessment of the software that powers IoT devices (firmware) to identify configuration and application vulnerabilities. This tool notifies users about the vulnerabilities discovered and assists in mitigating those in a timely manner.
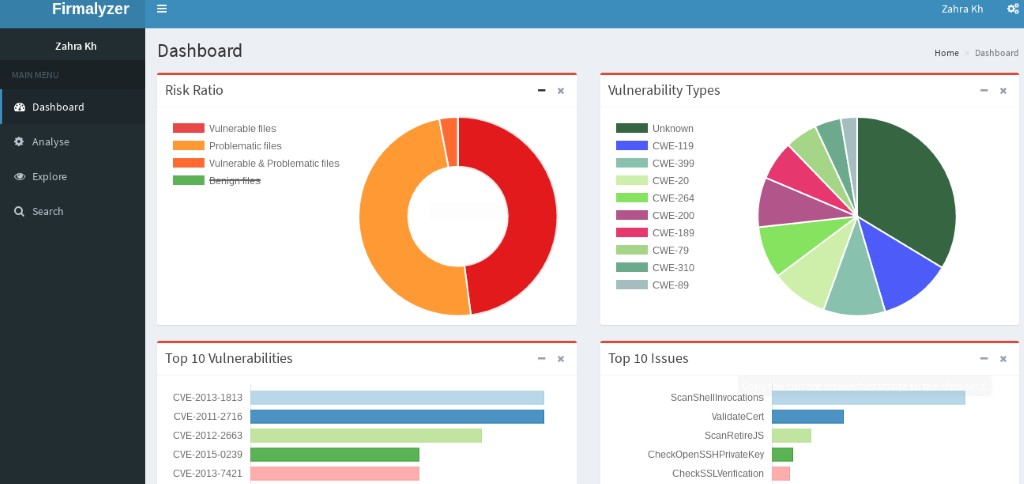
Figure 10.12: Screenshot of Firmalyzer
Listed below are some additional tools to perform IoT hacking:
RIoT Vulnerability Scanner (https://www.beyondtrust.com)
Foren6 (https://cetic.github.io)
IoT Inspector (https://www.iot-inspector.com)
RFCrack (https://github.com)
HackRF One (https://greatscottgadgets.com)