IoT technology is growing so quickly that it has become ubiquitous. With numerous applications and features but a lack of basic security policies, IoT devices are currently easy prey for hackers. In addition, upgrades to IoT devices have introduced new security flaws that can be easily exploited by hackers. To overcome this significant issue, manufacturing companies should consider security as the top priority, starting with planning and design, and up to deployment, implementation, management, and maintenance.
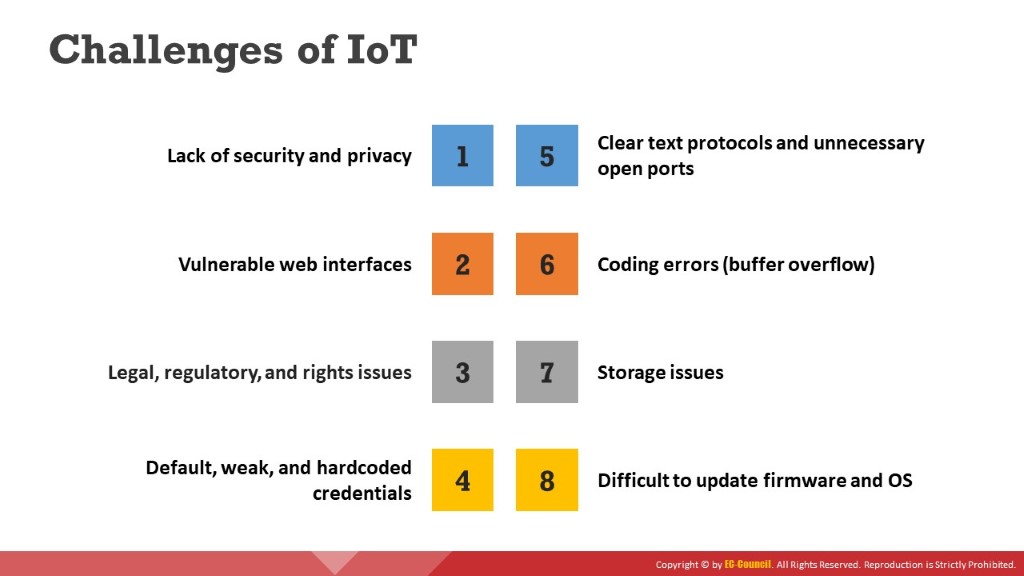
Discussed below are some of the challenges facing IoT devices that make them vulnerable to threats:
- Lack of Security and Privacy: Most IoT devices today, such as household devices, industrial devices, healthcare devices, automobiles, etc., are connected to the Internet and contain important and confidential data. These devices lack even basic security and privacy policies, and hackers can exploit this to carry out malicious activity.
- Vulnerable Web Interfaces: Many IoT devices come with embedded web server technology that makes them vulnerable to attacks.
- Legal, Regulatory, and Rights Issue: Due to the interconnection of IoT devices, certain security issues are raised with no existing laws that address these issues.
- Default, Weak, and Hardcoded Credentials: One of the most common reasons for cyber-attacks on IoT devices is their authentication systems. These devices usually come with default and weak credentials, which can easily be exploited by a hacker to gain unauthorized access to the devices.
- Clear Text Protocols and Unnecessary Open Ports: IoT devices lack encryption techniques during the transmission of data, which at times causes them to use certain protocols that transmit data in clear text in addition to having open ports.
- Coding Errors (Buffer Overflow): Most IoT devices today have embedded web services that are subject to the same vulnerabilities that are commonly exploited on web service platforms. As a result, updating such functionality may give rise to issues like buffer overflows, SQL injection, etc. within technology infrastructure.
- Storage Issues: IoT devices generally come with smaller data storage capacity, but the data collected and transmitted by the devices is limitless. Therefore, this gives rise to data storage, management, and protection issues.
- Difficult-to-Update Firmware and OS: Upgrading firmware is an essential step toward countering vulnerabilities in a device, but it may impair a device’s functionality. For this reason, developers or manufacturers may hesitate or even refuse to provide product support or make adjustments during the development phase of their products.
- Interoperability Standard Issues: One of the biggest obstacles for IoT devices is the interoperability issue, which is key to the viability and long-term growth of the entire IoT ecosystem. The issues that arise due to lack of interoperability in IoT devices are the inability of manufacturers to test application programming interfaces (APIs) using common methods and mechanisms, their inability to secure devices using software from third parties, and their inability to manage and monitor devices using a common layer.
- Physical Theft and Tampering: Physical attacks on IoT devices include tampering with the devices to inject malicious code or files to make the devices work the way the attacker intends, or making hardware modifications to the devices. Counterfeiting the devices may also be an issue when proper physical protection is not present to shield the devices.
- Lack of Vendor Support for Fixing Vulnerabilities: The firmware of the devices has to be upgraded in order to protect the devices against certain vulnerabilities, but vendors are hesitant, or they usually refuse to get third-party access to their devices.
- Emerging Economy and Development Issues: With widespread opportunities for IoT devices in every field, multiple layers of complexity are added for policymakers. The new landscape introduced by these devices adds a new dimension for the policymakers, who have to design new blueprints and policies for IoT devices.
- Handling of Unstructured Data: An increase in the number of connected devices will increase the complexity of handling unstructured data as its volume, velocity, and variety increases. It is important for organizations to understand and determine which data is valuable and actionable.
Source: https://www.owasp.org
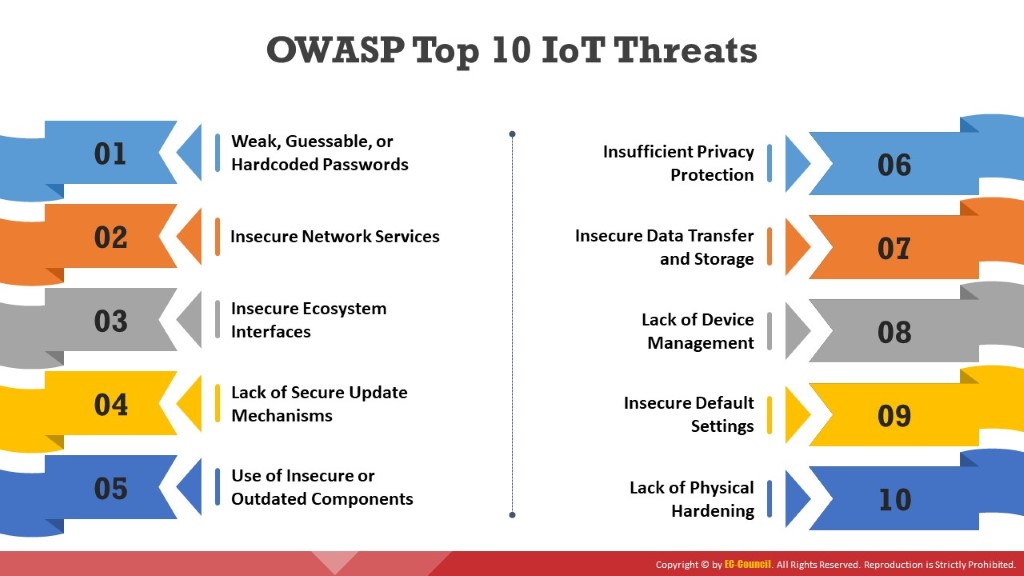
The Top 10 IoT threats, according to the Open Web Application Security Project (OWASP), are listed below:
- Weak, Guessable, or Hardcoded Passwords
Using weak, guessable, or hardcoded passwords allows publicly available or unchangeable credentials to be determined via brute forcing. This also includes backdoors in the firmware or client software that lead to unauthorized access to the deployed devices. - Insecure Network Services
Insecure network services are prone to various attacks like buffer overflow attacks, which cause a denial-of-service scenario, thus leaving the device inaccessible to the user. An attacker uses various automated tools such as port scanners and fuzzers to detect the open ports and exploit them to gain unauthorized access to services.
These insecure network services that are open to the Internet may compromise the confidentiality, authenticity, integrity, or availability of information and also allow remote access to critical information. - Insecure Ecosystem Interfaces
Insecure ecosystem interfaces such as web, backend API, mobile, and cloud interfaces outside the device lead to compromised security of the device and its components. Common vulnerabilities in such interfaces include lack of authentication/authorization, lack of encryption or weak encryption, and lack of input/output filtering. - Lack of Secure Update Mechanisms
Lack of secure update mechanisms, such as a lack of firmware validation on the device, lack of secure delivery, lack of anti-rollback mechanisms, or lack of notifications of security changes, may be exploited to perform various attacks. - Use of Insecure or Outdated Components
Use of outdated or older versions of software components or libraries, such as insecure customization of OS platforms or use of third-party hardware or software components from a compromised supply chain, may allow the devices themselves to be compromised. - Insufficient Privacy Protection
Insufficient privacy protection allows the user’s personal information stored on the devices or ecosystem to be compromised. - Insecure Data Transfer and Storage
Lack of encryption and access control of data that is in transit or at rest may result in leakage of sensitive information to malicious users. - Lack of Device Management
Lack of appropriate security support through device management on devices deployed in production, including asset management, update management, secure decommissioning, system monitoring, and response capabilities, may open the door to various attacks. - Insecure Default Settings
Insecure or insufficient device settings restrict the operators from modifying configurations to make the device more secure. - Lack of Physical Hardening
Lack of physical hardening measures allows potential attackers to acquire sensitive information that helps them in performing a remote attack or obtaining local control of the device.
IoT devices have very few security protection mechanisms against various emerging threats. These devices can be infected by malware or malicious code at an alarming rate. Attackers often exploit these poorly protected devices on the Internet to cause physical damage to the network, to wiretap the communication, and also to launch disruptive attacks such as DDoS.
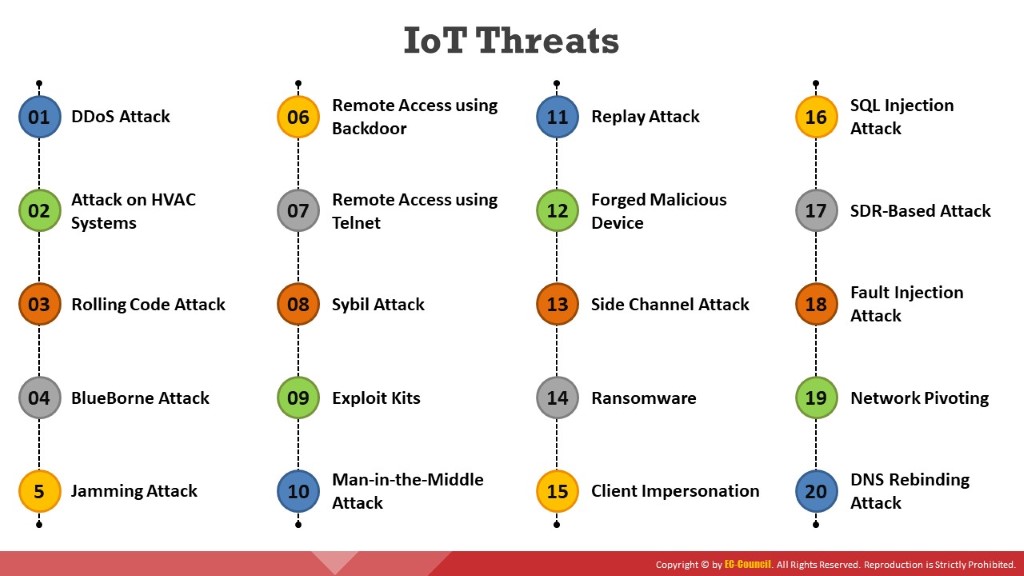
Listed below are some types of IoT attack:
DDoS Attack: An attacker converts the devices into an army of botnets to target a specific system or server, making it unavailable to provide services.
Attack on HVAC Systems: HVAC system vulnerabilities are exploited by attackers to steal confidential information such as user credentials and to perform further attacks on the target network.
Rolling Code Attack: An attacker jams and sniffs the signal to obtain the code transferred to a vehicle’s receiver; the attacker then uses it to unlock and steal the vehicle.
BlueBorne Attack: Attackers connect to nearby devices and exploit the vulnerabilities of the Bluetooth protocol to compromise the device.
Jamming Attack: An attacker jams the signal between the sender and the receiver with malicious traffic that makes the two endpoints unable to communicate with each other.
Remote Access using Backdoor: Attackers exploit vulnerabilities in the IoT device to turn it into a backdoor and gain access to an organization’s network.
Remote Access using Telnet: Attackers exploit an open telnet port to obtain information that is shared between the connected devices, including their software and hardware models.
Sybil Attack: An attacker uses multiple forged identities to create a strong illusion of traffic congestion, affecting communication between neighboring nodes and networks.
Exploit Kits: A malicious script is used by the attackers to exploit poorly patched vulnerabilities in an IoT device.
Man-in-the-Middle Attack: An attacker pretends to be a legitimate sender who intercepts all the communication between the sender and receiver and hijacks the communication.
Replay Attack: Attackers intercept legitimate messages from valid communication and continuously send the intercepted message to the target device to perform a denial-of-service attack or crash the target device.
Forged Malicious Device: Attackers replace authentic IoT devices with malicious devices if they have physical access to the network.
Side-Channel Attack: Attackers perform side-channel attacks by extracting information about encryption keys by observing the emission of signals, i.e., “side channels”, from IoT devices.
Ransomware Attack: Ransomware is a type of malware that uses encryption to block a user’s access to his/her device either by locking the screen or by locking the user’s files.
Client Impersonation: An attacker masquerades as a legitimate smart device/server using a malicious device and compromises an IoT client device by impersonating it, to perform unauthorized activities or access sensitive information on behalf of the legitimate client.
SQL Injection Attack: Attackers perform SQL injection attacks by exploiting vulnerabilities in the mobile or web applications used to control the IoT devices, to gain access to the devices and perform further attacks on them.
SDR-Based Attack: Using a software-based radio communication system, an attacker can examine the communication signals passing through the IoT network and can send spam messages to the interconnected devices.
Fault Injection Attack: A fault injection attack occurs when an attacker tries to introduce fault behavior in an IoT device, with the goal of exploiting these faults to compromise the security of that device.
Network Pivoting: An attacker uses a malicious smart device to connect and gain access to a closed server, and then uses that connection to pivot other devices and network connections to the server to steal sensitive information.
DNS Rebinding Attack: DNS rebinding is a process of obtaining access to a victim’s router using a malicious JavaScript code injected on a web page.