
Attackers can use tools such as Burp Suite, OWASP ZAP, and bettercap to hijack a session between a client and server. Discussed below are various tools that help perform session hijacking.
-
-
- OWASP ZAP
-
Source: https://owasp.org
OWASP Zed Attack Proxy (ZAP) is an integrated penetration testing tool for finding vulnerabilities in web applications. It offers automated scanners as well as a set of tools that make it possible to find security vulnerabilities manually. It is designed to be used by people with a wide range of security experience and is ideal for developers and functional testers who are new to penetration testing.
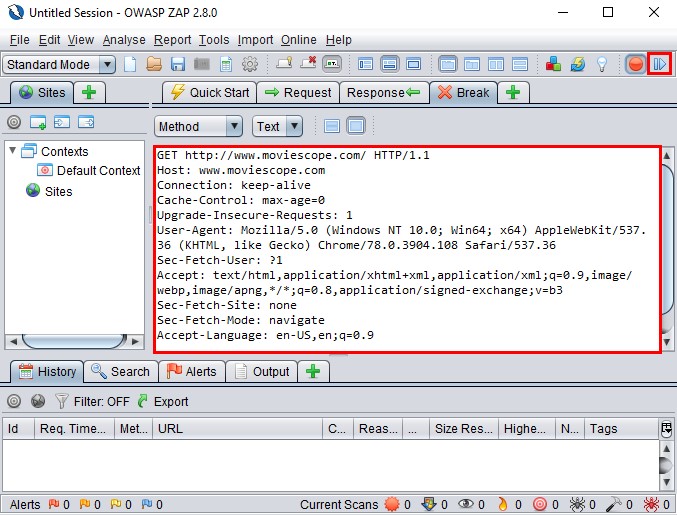
Figure 6.44: Screenshot of Burp Suite
The following are some additional session hijacking tools:
- Burp Suite (https://portswigger.net)
- bettercap (https://www.bettercap.org)
- netool toolkit (https://sourceforge.net)
- WebSploit Framework (https://sourceforge.net)
- sslstrip (https://pypi.org)
-
-
- Wireshark
-
Source: https://www.wireshark.org
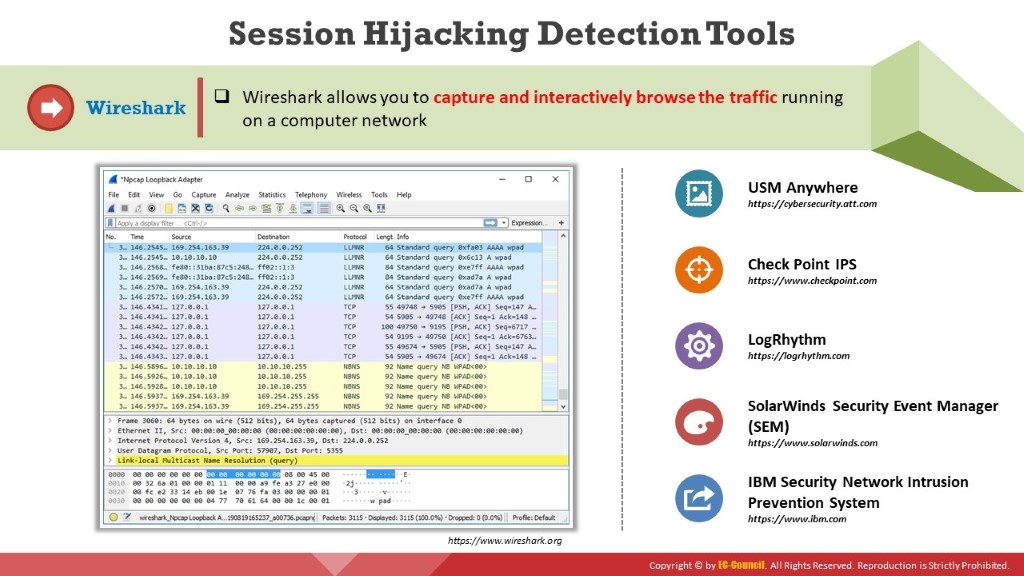
Wireshark allows users to capture and interactively browse the traffic on a network. This tool uses Winpcap to capture packets. Therefore, it can only capture packets on the networks supported by Winpcap. It captures live network traffic from Ethernet, IEEE 802.11, Point-to-Point Protocol/High-level Data Link Control (PPP/HDLC), Asynchronous Transfer Mode (ATM), Bluetooth, Universal Serial Bus (USB), Token Ring, Frame Relay, and Fiber Distributed Data Interface (FDDI) networks. Security professionals use Wireshark to monitor and detect session hijacking attempts.

Figure 6.46: Screenshot of Wireshark
The following are some additional session hijacking detection tools:
- USM Anywhere (https://cybersecurity.att.com)
- Check Point IPS (https://www.checkpoint.com)
- LogRhythm (https://logrhythm.com)
- SolarWinds Security Event Manager (SEM) (https://www.solarwinds.com)
- IBM Security Network Intrusion Prevention System (https://www.ibm.com)