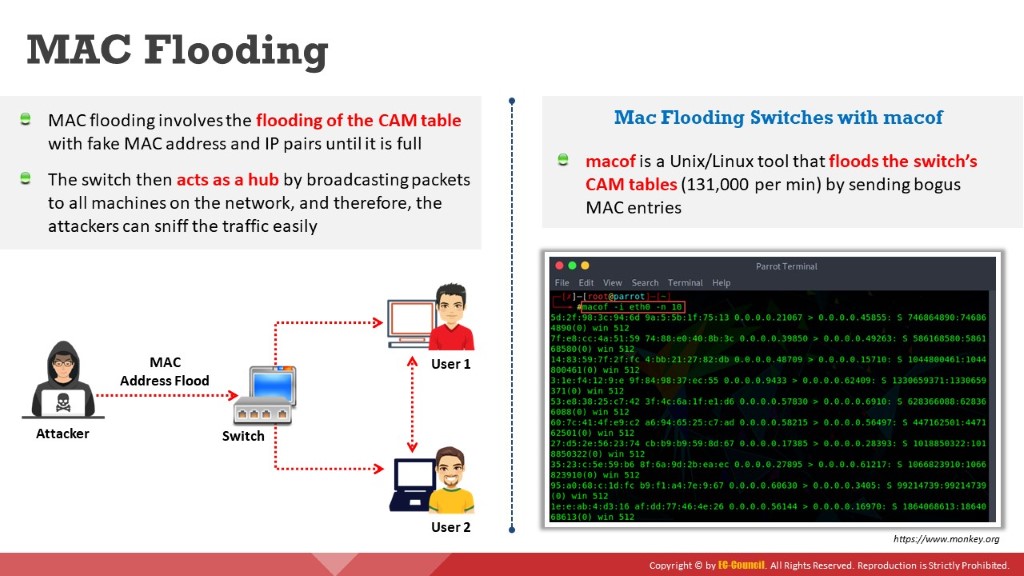
MAC flooding is a technique used to compromise the security of network switches that connect network segments or devices. Attackers use the MAC flooding technique to force a switch to act as a hub so that they can easily sniff the traffic.
In a switched network, an Ethernet switch contains a CAM table that stores all the MAC addresses of devices connected in the network. A switch acts as an intermediate device between one or more computers in a network. It looks for Ethernet frames, which carry the destination MAC address; then, it tallies this address with the MAC address in its CAM table and forwards the traffic to the destined machine. Unlike a hub, which broadcasts data across the network, a switch sends data only to the intended recipient. Thus, a switched network is more secure compared to a hub network. However, the size of the CAM table is fixed, and as it can store only a limited number of MAC addresses in it, an attacker may send numerous fake MAC address to the switch. No problem occurs until the MAC address table is full. Once the MAC address table is full, any further requests may force the switch to enter fail-open mode. In the fail-open mode, the switch starts behaving like a hub and broadcasts incoming traffic through all the ports in the network. The attacker then changes his/her machine’s NIC to promiscuous mode to enable the machine to accept all the traffic entering it. Thus, attackers can sniff the traffic easily and steal sensitive information.

Figure 6.10: MAC flooding
MAC Flooding Switches with macof
Source: https://www.monkey.org
macof is a Unix/Linux tool that is a part of the dsniff collection. It floods the local network with random MAC and IP addresses, causing some switches to fail and open in repeating mode, thereby facilitating sniffing. This tool floods the switch’s CAM tables (131,000 per min) by sending forged MAC entries. When the MAC table fills up, and the switch converts to hub-like operation, an attacker can monitor the data being broadcast.

Figure 6.11: MAC flooding using macof
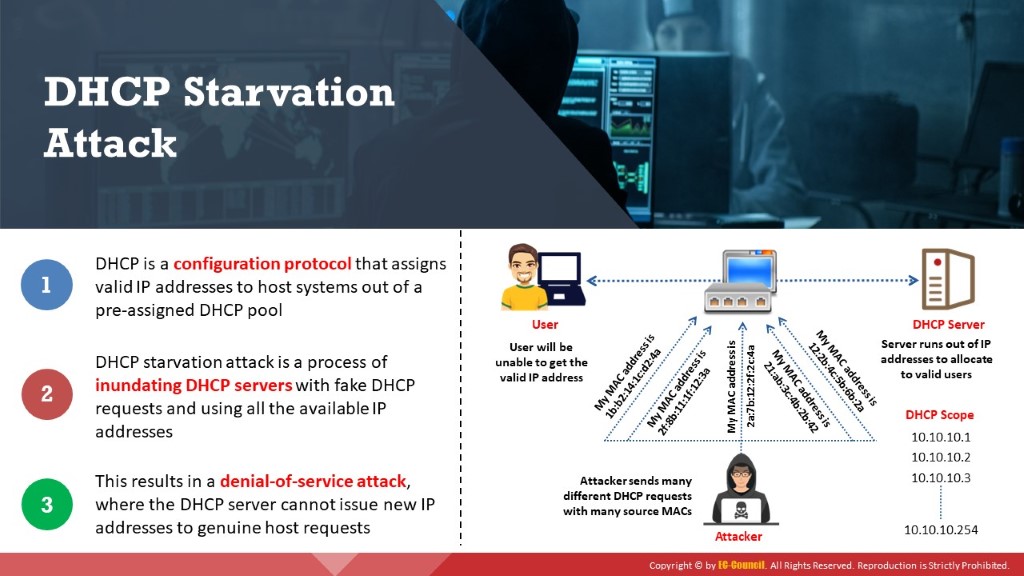
DHCP is a configuration protocol that assigns valid IP addresses to host systems from a pre-assigned DHCP pool. In a DHCP starvation attack, an attacker floods the DHCP server by sending numerous DHCP requests and uses all available IP addresses that the DHCP server can issue. As a result, the server cannot issue any more IP addresses, leading to a DoS attack. Because of this issue, valid users cannot obtain or renew their IP addresses; thus, they fail to access their network. An attacker broadcasts DHCP requests with spoofed MAC addresses with the help of tools such as Yersinia, Hyenae, and Gobbler.
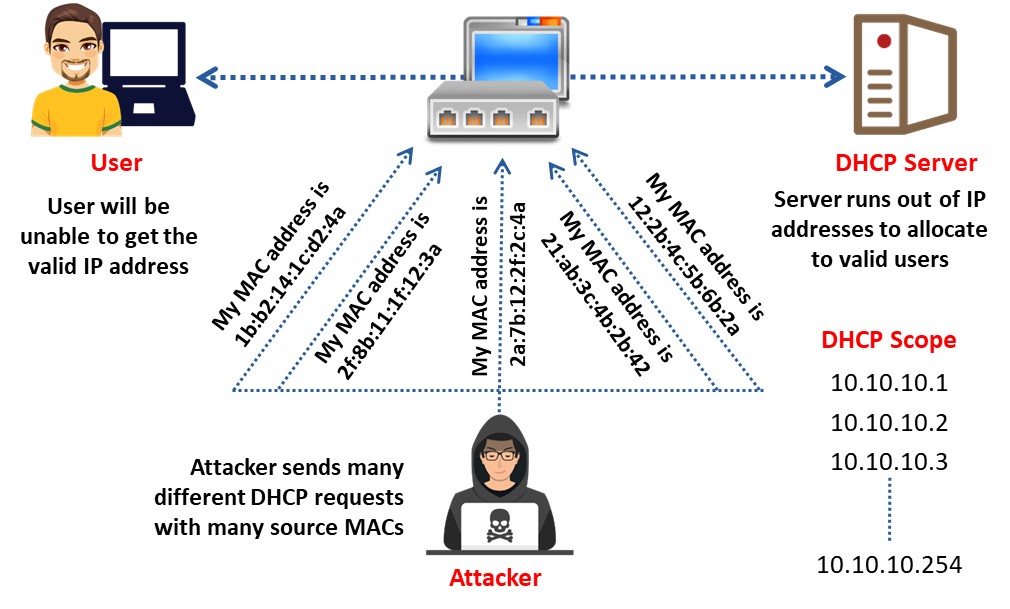
Figure 6.12: DHCP starvation attack

Address resolution protocol (ARP) is a protocol used for mapping an IP address to a physical machine address that is recognized in the local network. ARP packets can be forged to send data to the attacker’s machine. ARP spoofing involves constructing a large number of forged ARP request and reply packets to overload a switch. When a machine sends an ARP request, it assumes that the ARP reply will come from the right machine. ARP provides no means of verifying the authenticity of the responding device. Even systems that have not made an ARP request can accept the ARP replies coming from other devices. Attackers use this flaw in ARP to create malformed ARP replies containing spoofed IP and MAC addresses. Assuming this to be the legitimate ARP reply, the victim’s computer blindly accepts the ARP entry into its ARP table. Once the ARP table is flooded with spoofed ARP replies, the switch is set to forwarding mode, and the attacker intercepts all the data that flows from the victim’s machine without the victim being aware of the attack. Attackers flood a target computer’s ARP cache with forged entries; this is also known as poisoning. ARP spoofing is an intermediary for performing attacks such as DoS, MITM, and session hijacking.
How does ARP Spoofing Work?
ARP spoofing is a method of attacking an Ethernet LAN. When a legitimate user initiates a session with another user in the same layer 2 broadcast domain, the switch broadcasts an ARP request using the recipient's IP address, while the sender waits for the recipient to respond with a MAC address. An attacker eavesdropping on this unprotected layer 2 broadcast domain can respond to the broadcast ARP request and replies to the sender by spoofing the intended recipient’s IP address. The attacker runs a sniffer and turns the machine’s NIC adapter to promiscuous mode.
ARP spoofing is a method of attacking an Ethernet LAN. It succeeds by changing the IP address of the attacker’s computer to that of the target computer. A forged ARP request and reply packet can find a place in the target ARP cache in this process. As the ARP reply has been forged, the destination computer (target) sends frames to the attacker’s computer, where the attacker can modify the frames before sending them to the source machine (User A) in an MITM attack. The attacker can also launch a DoS attack by associating a non-existent MAC address to the IP address of the gateway; alternatively, the attacker may sniff the traffic passively and then forward it to the target destination.

Figure 6.13: Working of an ARP spoofing attack
-
-
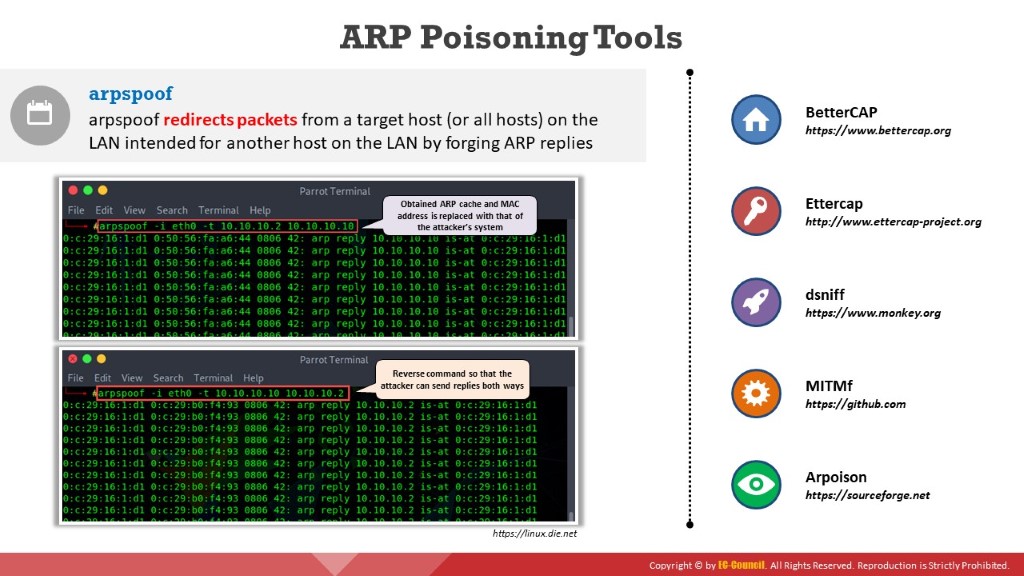
- arpspoof
-
Source: https://linux.die.net
arpspoof redirects packets from a target host (or all hosts) on the LAN intended for another host on the LAN by forging ARP replies. This is an extremely effective way of sniffing traffic on a switch.
Syntax:
arpspoof –i [Interface] –t [Target Host]
As shown in the screenshot, attackers use the arpspoof tool to obtain the ARP cache; then, the MAC address is replaced with that of an attacker’s system. Therefore, any traffic flowing from the victim to the gateway will be redirected to the attacker’s system.
Further, an attacker can issue the same command in reverse as he/she is in the middle and can send ARP replies in both directions.
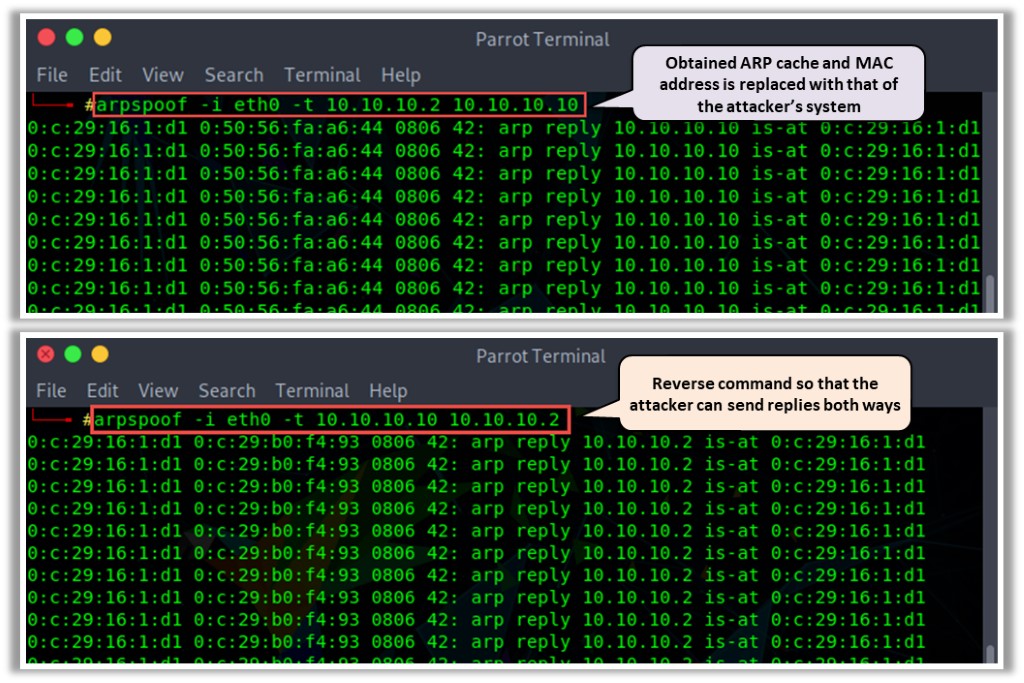
Figure 6.14: Screenshots of arpspoof
Some examples of ARP poisoning tools are listed below:
- BetterCAP (https://www.bettercap.org)
- Ettercap (http://www.ettercap-project.org)
- dsniff (https://www.monkey.org)
- MITMf (https://github.com)
- Arpoison (https://sourceforge.net
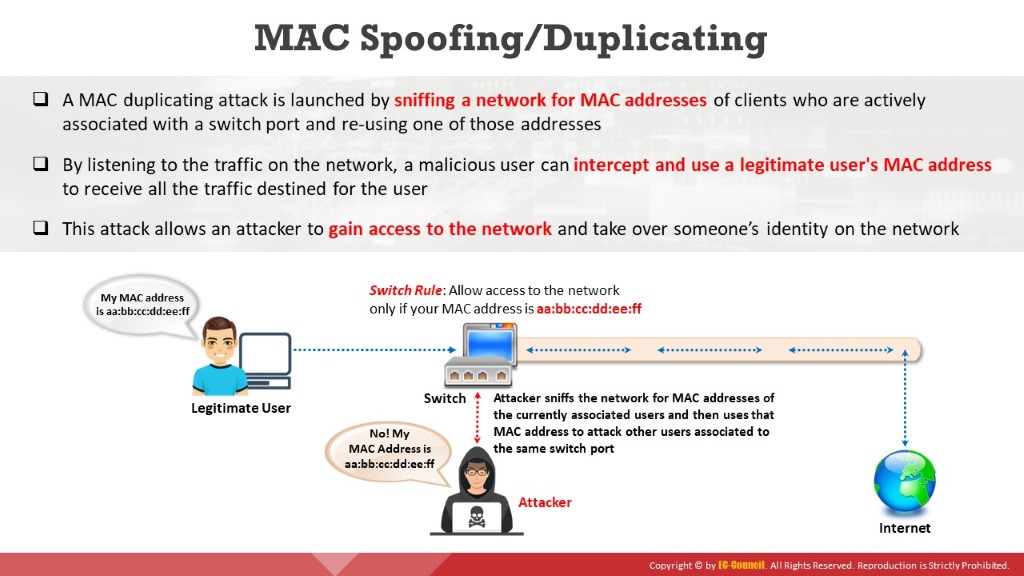
MAC duplicating refers to spoofing a MAC address with the MAC address of a legitimate user on the network. A MAC duplicating attack involves sniffing a network for MAC addresses of legitimate clients connected to the network. In this attack, the attacker first retrieves the MAC addresses of clients who are actively associated with the switch port. Then, the attacker spoofs a MAC address with the MAC address of the legitimate client. If the spoofing is successful, then the attacker can receive all the traffic destined for the client. Thus, an attacker can gain access to the network and take over the identity of someone on the network.
The diagram shows how an attacker performs a MAC spoofing/duplicating attack.

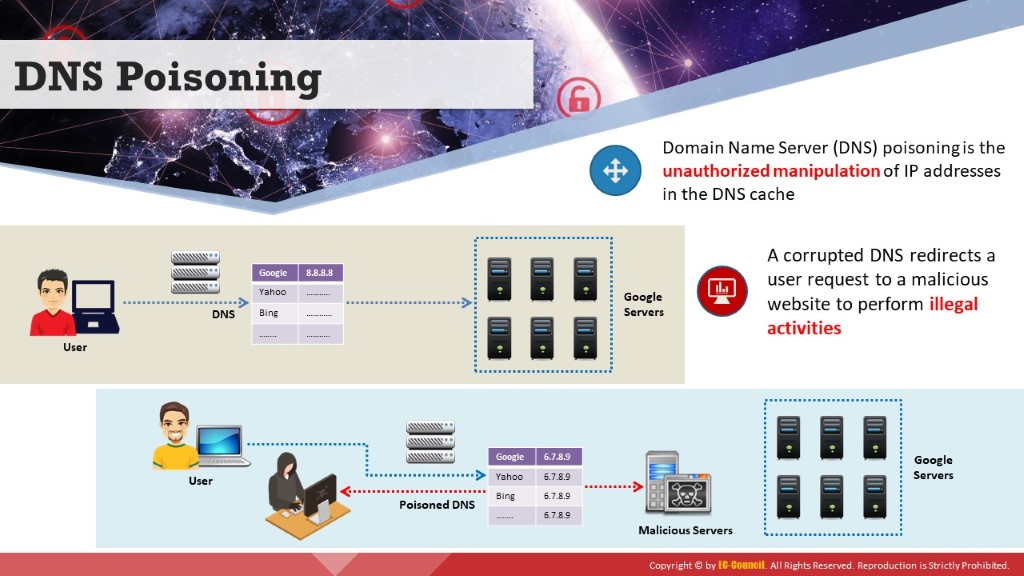
DNS is the protocol that translates a domain name (e.g., www.eccouncil.org) into an IP address (e.g., 208.66.172.56). The protocol uses DNS tables that contain the domain name and its equivalent IP address stored in a distributed large database. In DNS poisoning, also known as DNS spoofing, the attacker tricks a DNS server into believing that it has received authentic information when, in reality, it has not received any. The attacker tries to redirect the victim to a malicious server instead of the legitimate server. The attacker does this by manipulating the DNS table entries in the DNS. This results in substitution of a false IP address at the DNS level, where web addresses are converted into numeric IP addresses.
When the victim tries to access a website, the attacker manipulates the entries in the DNS table so that the victim’s system redirects the URL to the attacker’s server. The attacker replaces IP address entries for a target site on a given DNS server with the IP address of the server (malicious server) he/she controls. The attacker can create fake DNS entries for the server (containing malicious content) with the same names as that of the target server. Thus, the victim connects to the attacker’s server without realizing it. For example, if a victim types ww.google.com, the request is redirected to the fake website www.goggle.com. Once the victim connects to the attacker’s server, the attacker can compromise the victim’s system and steal data.
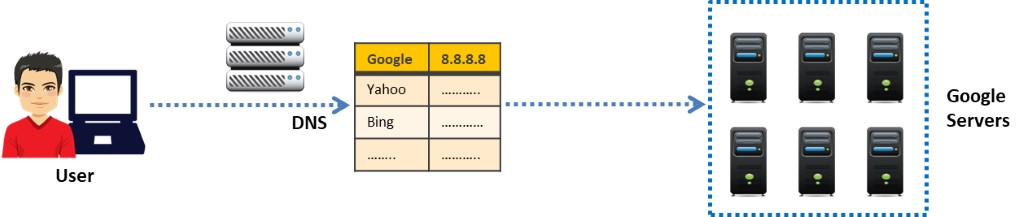
Figure 6.16: Illustration of a normal DNS request
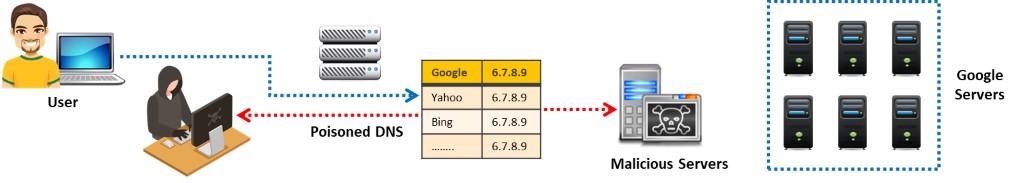
Figure 6.17: Illustration of a poisoned DNS request

System administrators use automated tools to monitor their network, but attackers misuse these tools to sniff network data.
-
-
Wireshark
-
Source: https://www.wireshark.org
Wireshark lets you capture and interactively browse the traffic running on a computer network. This tool uses WinPcap to capture packets on its own supported networks. It captures live network traffic from Ethernet, IEEE 802.11, PPP/HDLC, ATM, Bluetooth, USB, Token Ring, Frame Relay, and FDDI networks. The captured files can be programmatically edited via the command-line. A set of filters for customized data display can be refined using a display filter.
As shown in the screenshot, attackers use Wireshark to sniff and analyze the packet flow in the target network and extract critical information about the target.
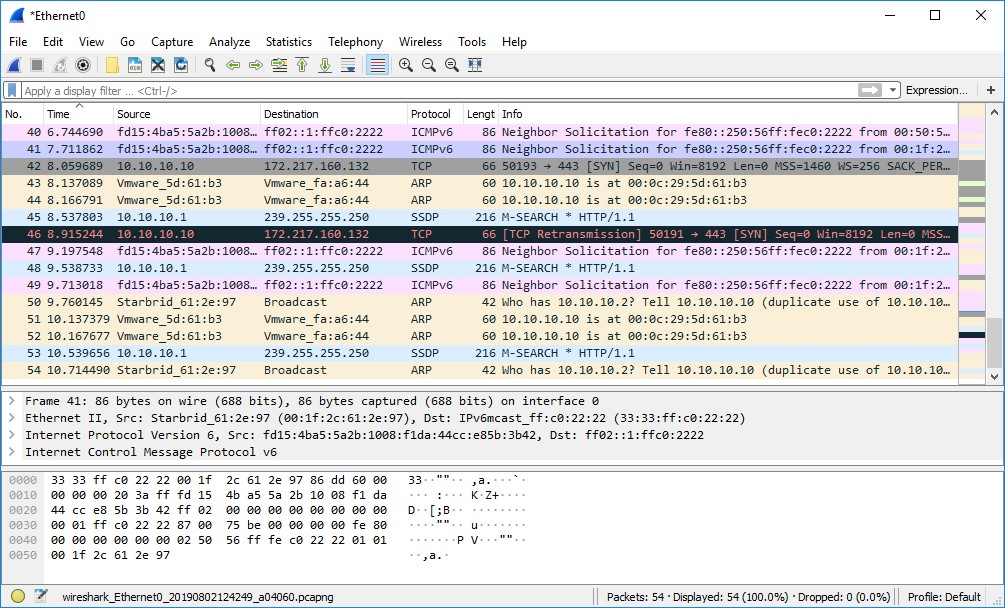
Figure 6.18: Capturing packets using Wireshark
Some examples of additional sniffing tools are listed below:
-
-
- SteelCentral Packet Analyzer (https://www.riverbed.com)
- Capsa Network Analyzer (https://www.colasoft.com)
- Observer Analyzer (https://www.viavisolutions.com)
- PRTG Network Monitor (https://www.paessler.com)
- SolarWinds Deep Packet Inspection and Analysis (https://www.solarwinds.com)
-