


Impersonation
Impersonation is a common human-based social engineering technique where an attacker pretends to be a legitimate or authorized person. Attackers perform impersonation attacks personally or use a phone or another communication medium to mislead their target and trick them into revealing information. The attacker might impersonate a courier or delivery person, janitor, businessman, client, technician, or they may pretend to be a visitor. Using this technique, the attacker gathers sensitive information by scanning terminals for passwords, searching for important documents on employees’ desks, rummaging through bins, and through other tactics. The attacker may even try to overhear confidential conversations and “shoulder surf” to obtain sensitive information.
Types of impersonation used in social engineering:
Posing as a legitimate end-user
Posing as an important user
Posing as a technical support agent
Posing as an internal employee, client, or vendor
Posing as a repairman
Abusing the over-helpfulness of the help desk
Posing as someone with third-party authorization
Posing as a tech support agent through vishing
Posing as a trusted authority
Some impersonation tricks that an attacker performs to gather sensitive information about the target organization exploit the human nature of trust, fear, and moral obligation.
Posing as a Legitimate End User
An attacker might impersonate an employee and then resort to deviant methods to gain access to privileged data. They may provide a false identity to obtain sensitive information.
Another example is when a “friend” of an employee asks them to retrieve information that a bedridden employee supposedly needs. There is a well-recognized rule in social interaction that a favor begets a favor, even if the original “favor” is offered without a request from the recipient. This is known as reciprocation. Corporate environments deal with reciprocation daily. Social engineers try to take advantage of this social trait via impersonation.
Example:
“Hi! This is John from the finance department. I have forgotten my password. Can I get it?”
Posing as an Important User
Another behavioral factor that aids a social engineer is people’s habit of not questioning authority. People often go out of their way for those whom they perceive to have authority. An attacker posing as an important individual — such as a vice president or director — can often manipulate an unprepared employee. Attackers who take impersonation to a higher level by assuming the identity of an important employee add an element of intimidation. The reciprocation factor also plays a role in this scenario where lower-level employees might go out of their way to help a higher-authority. For example, it is less likely that a help-desk employee will turn down a request from a vice president who is hard-pressed for time and needs some vital information for a meeting. In case an employee refuses to divulge information, social engineers may use authority to intimidate employees and may even threaten to report the employee’s misconduct to their supervisors. This technique assumes greater significance when the attacker considers it a challenge to get away with impersonating an authority figure.
Example:
“Hi! This is Kevin, the CFO’s Secretary. I’m working on an urgent project, and I forgot my system password. Can you help me out?”
Posing as a Technical Support Agent
Another technique involves an attacker masquerading as a technical support agent, particularly when the victim is not proficient in technical areas. The attacker may pretend to be a hardware vendor, a technician, or a computer supplier. One demonstration at a hacker meeting had the speaker calling Starbucks and asking its employees whether their broadband connection was properly working. The perplexed employee replied that it was the modem that was giving them trouble. The hacker, without giving any credentials, went on to make him read out the credit card number of the last transaction. In a corporate scenario, the attacker may ask employees to reveal their login information, including their password, to fix a nonexistent problem.
Example:
“Sir, this is Mathew, technical support at X Company. Last night we had a system crash here, and we are checking for lost data. Can you give me your ID and password?”
Posing as an Internal Employee, Client, or Vendor
The attacker usually dresses up in business clothes or another suitable uniform. They enter an organization’s building while pretending to be a contractor, client, service personnel, or another authorized person. Then they roam around unnoticed and look for passwords stuck on terminals, extract critical data from wastepaper bins, papers lying on desks, and perform other information gathering. The attacker may also implement other social engineering techniques such as shoulder surfing (observing users typing login credentials or other sensitive information) and eavesdropping (purposely overhearing confidential conversations between employees) to gather sensitive information that might help launch an attack on the organization.
Repairman
Computer technicians, electricians, and telephone repairpersons are generally unsuspected people. Attackers might impersonate a technician or repair person and enter the organization. They perform normal activities associated with their assumed duty while looking for hidden passwords, critical information on desks, information in trash bins, and other useful information; they sometimes even plant snooping devices in hidden locations.
Impersonation (Vishing)
Vishing (voice or VoIP phishing) is an impersonation technique in which the attacker uses Voice over IP (VoIP) technology to trick individuals into revealing their critical financial and personal information and uses the information for financial gain. The attacker uses caller ID spoofing to forge identification. In many cases, Vishing includes pre-recorded messages and instructions resembling a legitimate financial institution. Through Vishing, the attacker tricks the victim into providing bank account or credit card details for identity verification over the phone.
The attacker may send a fake SMS or email message to the victim, asking the victim to call the financial institution for credit card or bank account verification. In some cases, the victim receives a voice call from the attacker. When the victim calls the number listed in the message or receives the attacker’s call, they hear recorded instructions that insist they provide personal and financial information like name, date of birth, social security number, bank account numbers, credit card numbers, or credentials like usernames, passwords. Once the victim provides the information, the recorded message confirms verification of the victim’s account.
Discussed below are some tricks attackers use when Vishing to gather sensitive information.
Abusing the Over-Helpfulness of Help Desk
Help desks are frequently targeted for social engineering attacks for a reason. The staff members are trained to be helpful, and they often give away sensitive information such as passwords and network information without verifying the authenticity of the caller.
The attacker should know employees’ names and have details about the person he is trying to impersonate to be effective. The attacker may call a company’s help desk pretending to be a senior official to try to extract sensitive information out of the help desk.
Example:
A man calls a company’s help desk and says he has forgotten his password. He adds that if he misses the deadline on a big advertising project, his boss might fire him.
The help desk worker feels sorry for him and quickly resets the password, unwittingly giving the attacker entrance into the corporate network.
Third-party Authorization
Another popular technique used by an attacker is to represent themself as an agent authorized by some senior authority in an organization to obtain information on their behalf.
For instance, when an attacker knows the name of the employee in the target organization authorized to access the required information, they keep a vigil on them so that they can access the required data in the absence of the concerned employee. In this case, the attacker can approach the help desk or other personnel in the company claiming that the employee (authority figure) has requested the information.
Even though there might be suspicion attached to the authenticity of the request, people tend to overlook this in favor of being helpful in the workplace. People tend to believe that others are being honest when they reference an important person and provide the required information.
This technique is effective, particularly when the authority figure is on vacation or traveling, making instant verification impossible.
Example:
“Hi, I am John, I spoke with Mr. XYZ last week before he went on vacation and he said that you would be able to provide me with the information in his absence. Could you help me out?”
Tech Support
Like the impersonation of a tech support agent above, an attacker can use vishing to pretend to be a technical support staff member of the target organization’s software vendor or contractor to obtain sensitive information. The attacker may pretend to troubleshoot a network problem and ask for the user ID and password of a computer to detect the problem. Believing them to be a troubleshooter, the user would provide the required information.
Example:
1) Attacker: “Hi, this is Mike from tech support. Some folks in your office have reported a slowdown in logging. Is this true?”
2) Employee: “Yes, it has seemed slow lately.”
3) Attacker: “Well, we have moved you to a new server, and your service should be much better now. If you want to give me your password, I can check your service. Things will be better from now on.”
Trusted Authority Figure
The most effective method of social engineering is posing as a trusted authority figure. An attacker might pretend to be a fire marshal, superintendent, auditor, director, or other important figure over the phone or in-person to obtain sensitive information from the target.
Example:
“Hi, I am John Brown. I'm with the external auditor, Arthur Sanderson. We've been requested by the corporate to do a surprise inspection of your disaster recovery procedures. Your department has 10 minutes to show me how you would recover from a website crash.”
“Hi, I'm Sharon, a sales rep out of the New York office. I know this is short notice, but I have a group of prospective clients out in the car, and I've been trying to get them to outsource their security training needs to us for months.
They're located just a few miles away, and I think that if I can give them a quick tour of our facilities, it would be enough to push them over the edge and get them to sign up.
Oh yeah, they are particularly interested in what security precautions we've adopted. It seems someone hacked into their website a while back, which is one of the reasons they're considering our company.”
“Hi, I'm with Aircon Express Services. We received a call that the computer room is getting too warm, so I need to check your HVAC system.” Using professional-sounding terms like HVAC (Heating, Ventilation, and Air Conditioning) may add just enough credibility to an intruder's masquerade to allow them to access the targeted secured resource.
Eavesdropping
Eavesdropping refers to an unauthorized person listening to a conversation or reading others’ messages. It includes the interception of any form of communication, including audio, video, or written, using channels such as telephone lines, email, and instant messaging. An attacker can obtain sensitive information such as passwords, business plans, phone numbers, and addresses.
Shoulder Surfing
Shoulder surfing is the technique of looking over someone’s shoulder as they key information into a device. Attackers use shoulder surfing to find out passwords, personal identification numbers, account numbers, and other information. They sometimes even use binoculars and other optical devices or install small cameras to record the actions performed on the victim’s system to obtain login details and other sensitive information.
Dumpster Diving
Dumpster diving is the process of retrieving sensitive personal or organizational information by searching through trash bins. Attackers can extract confidential data such as user IDs, passwords, policy numbers, network diagrams, account numbers, bank statements, salary data, source code, sales forecasts, access codes, phone lists, credit card numbers, calendars, and organizational charts on paper or disk. Attackers can then use this information to perform various malicious activities. Sometimes attackers even use pretexts to support their dumpster diving initiatives, such as impersonating a repair person, technician, cleaner, or other legitimate worker.
Information that attackers can obtain by searching through trash bins includes:
Phone lists: Disclose employees’ names and contact numbers.
Organizational charts: Disclose details about the structure of the company, physical infrastructure, server rooms, restricted areas, and other organizational data.
Email printouts, notes, faxes, and memos: Reveal personal details of an employee, passwords, contacts, inside working operations, certain useful instructions, and other data.
Policy manuals: Reveal information regarding employment, system use, and operations.
Event notes, calendars, or computer use logs: Reveal information regarding the user’s log on and off timings, which helps the attacker to decide on the best time to plan their attack.
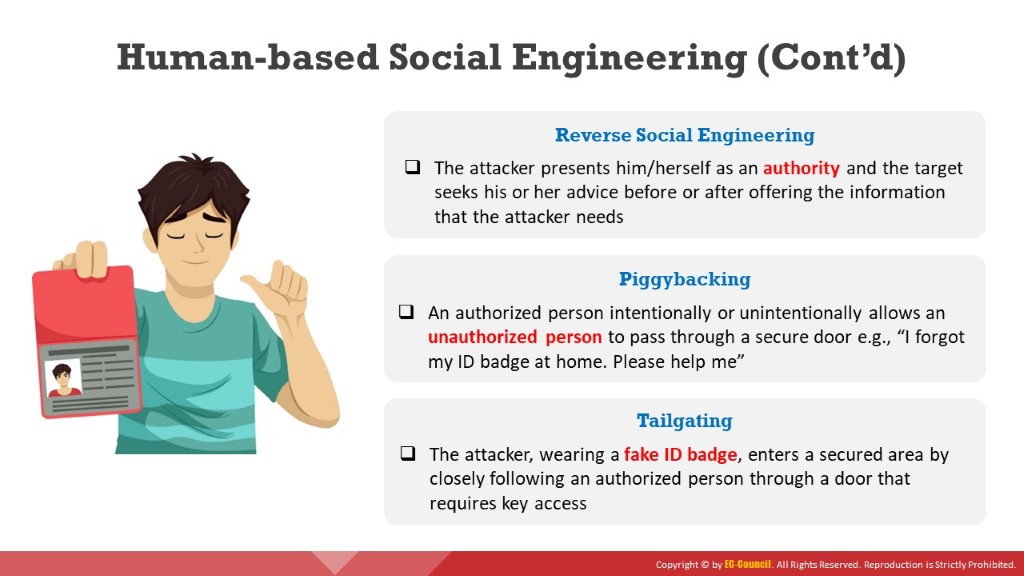
Reverse Social Engineering
Generally, reverse social engineering is difficult to carry out. This is primarily because its execution needs a lot of preparation and skills. In reverse social engineering, a perpetrator assumes the role of a knowledgeable professional so that the organization’s employees ask them for information. The attacker usually manipulates questions to draw out the required information.
First, the social engineer will cause an incident, creating a problem, and then present themself as the problem solver through general conversation, encouraging employees to ask questions. For example, an employee may ask how this problem has affected files, servers, or equipment. This provides pertinent information to the social engineer. Many different skills and experiences are required to carry out this tactic successfully.
Provided below are some of the techniques involved in reverse social engineering:
Sabotage: Once the attacker gains access, they will corrupt the workstation or make it appear corrupted. Under such circumstances, users seek help as they face problems.
Marketing: To ensure that the user calls the attacker, the attacker must advertise. The attacker can do this either by leaving their business card in the target’s office or by placing their contact number on the error message itself.
Support: Even if the attacker has already acquired the desired information, they may continue to assist the users so that they remain ignorant of the hacker’s identity.
A good example of a reverse social engineering virus is the “My Party” worm. This virus does not rely on sensational subject lines but rather makes use of inoffensive and realistic names for its attachments. By using realistic words, the attacker gains the user’s trust, confirms the user’s ignorance, and completes the task of information gathering.
Piggybacking
Piggybacking usually implies entry into a building or security area with the consent of the authorized person. For example, an attacker might request an authorized person to unlock a security door, saying that they have forgotten their ID badge. In the interest of common courtesy, the authorized person will allow the attacker to pass through the door.