Due to the growing severity of cyber-attacks, vulnerability research has become critical as it helps to mitigate the chance of attacks. Vulnerability research provides awareness of advanced techniques to identify flaws or loopholes in the software that can be exploited by attackers. Vulnerability scoring systems and vulnerability databases are used by security analysts to rank information system vulnerabilities and to provide a composite score of the overall severity and risk associated with identified vulnerabilities. Vulnerability databases collect and maintain information about various vulnerabilities present in information systems.
Following are some of the vulnerability scoring systems and databases:
Common Vulnerability Scoring System (CVSS)
Common Vulnerabilities and Exposures (CVE)
National Vulnerability Database (NVD)
Common Weakness Enumeration (CWE)
Common Vulnerability Scoring System (CVSS)
Source: https://www.first.org, https://nvd.nist.gov
CVSS is a published standard that provides an open framework for communicating the characteristics and impacts of IT vulnerabilities. The system’s quantitative model ensures repeatable, accurate measurement while enabling users to see the underlying vulnerability characteristics that were used to generate the scores. Thus, CVSS is well suited as a standard measurement system for industries, organizations, and governments that need accurate and consistent vulnerability impact scores. Two common uses of CVSS are prioritizing vulnerability remediation activities and calculating the severity of vulnerabilities discovered on one’s systems. The National Vulnerability Database (NVD) provides CVSS scores for almost all known vulnerabilities.
CVSS helps capture the principal characteristics of a vulnerability and produce a numerical score to reflect its severity. This numerical score can thereafter be translated into a qualitative representation (such as low, medium, high, or critical) to help organizations properly assess and prioritize their vulnerability management processes.
CVSS assessment consists of three metrics for measuring vulnerabilities:
Base Metric: Represents the inherent qualities of a vulnerability
Temporal Metric: Represents the features that continue to change during the lifetime of the vulnerability.
Environmental Metric: Represents vulnerabilities that are based on a particular environment or implementation.
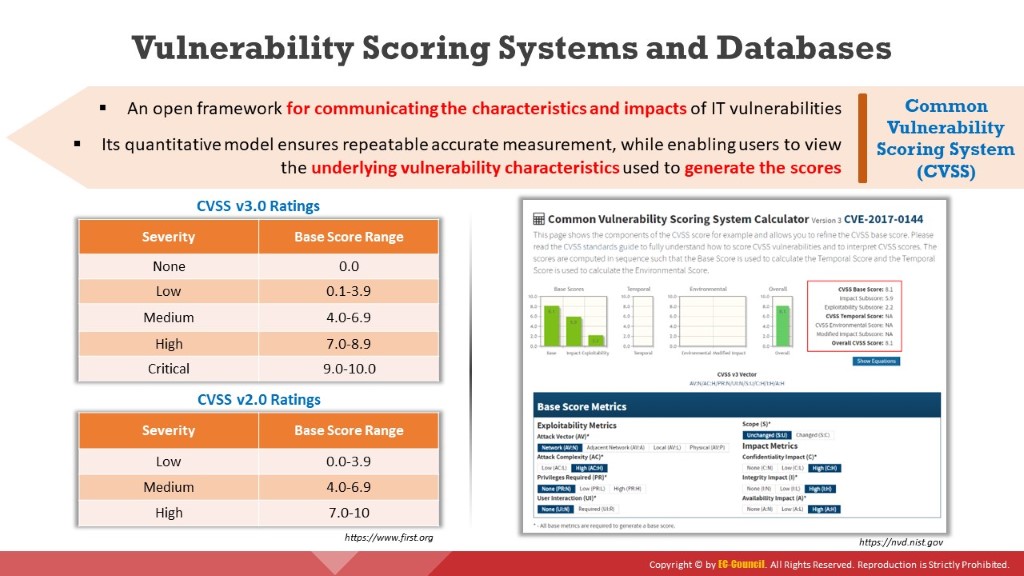
Each metric sets a score from 1–10, with 10 being the most severe. The CVSS score is calculated and generated by a vector string, which represents the numerical score for each group in the form of a block of text. The CVSS calculator ranks the security vulnerabilities and provides the user with information on the overall severity and risk related to the vulnerability.
|
Severity |
Base Score Range |
|
None |
0.0 |
|
Low |
0.1-3.9 |
|
Medium |
4.0-6.9 |
|
High |
7.0-8.9 |
|
Critical |
9.0-10.0 |
Table 3.6: CVSS v3.0 ratings
|
Severity |
Base Score Range |
|
Low |
0.0-3.9 |
|
Medium |
4.0-6.9 |
|
High |
7.0-10 |
Table 3.7: CVSS v2.0 ratings
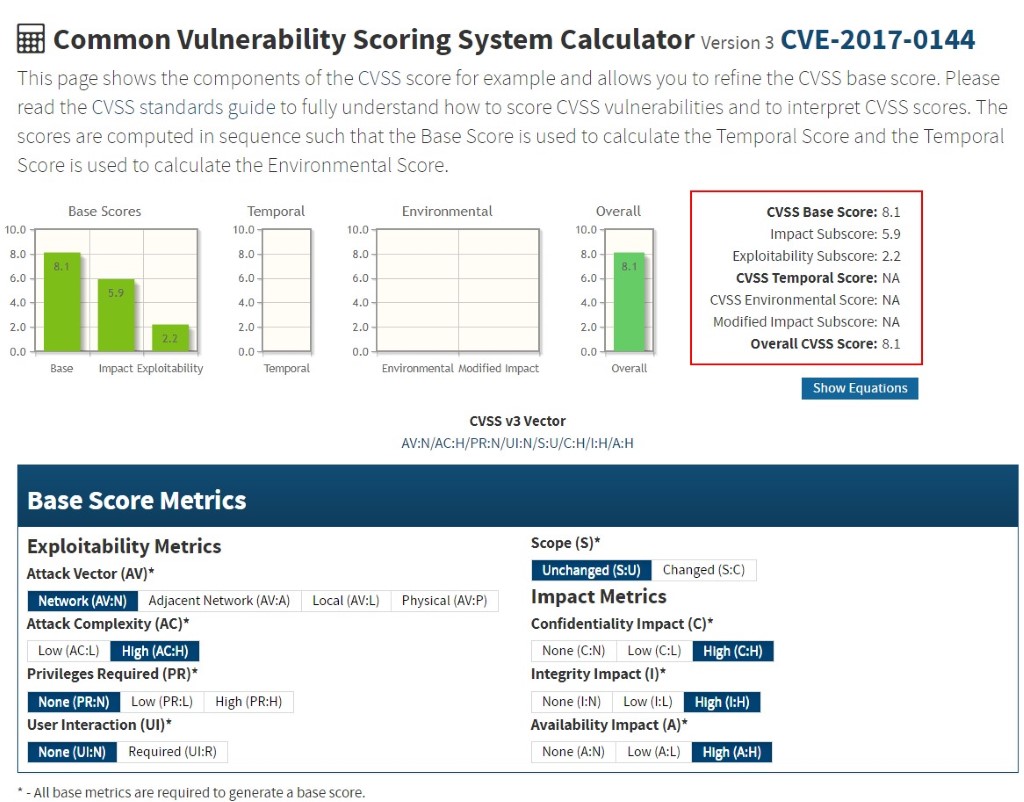
Figure 3.13: Common Vulnerability Scoring System Calculator Version 3
Common Vulnerabilities and Exposures (CVE)
Source: https://cve.mitre.org
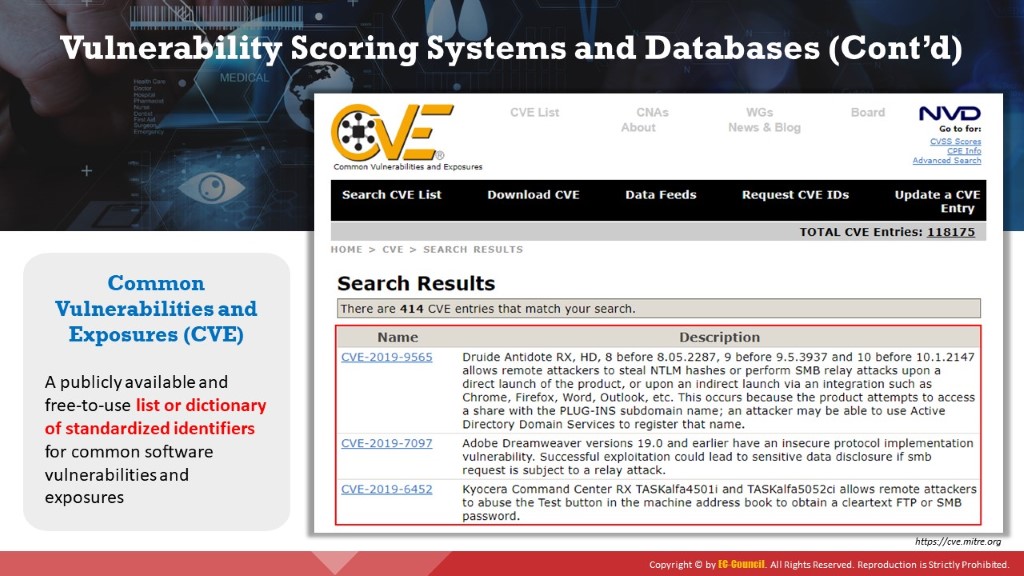
CVE® is a publicly available and free-to-use list or dictionary of standardized identifiers for common software vulnerabilities and exposures. The use of CVE Identifiers, or “CVE IDs,” which are assigned by CVE Numbering Authorities (CNAs) from around the world, ensures confidence among parties when discussing or sharing information about a unique software or firmware vulnerability. CVE provides a baseline for tool evaluation and enables data exchange for cybersecurity automation. CVE IDs provide a baseline for evaluating the coverage of tools and services so that users can determine which tools are most effective and appropriate for their organization’s needs. In short, products and services compatible with CVE provide better coverage, easier interoperability, and enhanced security.
What CVE is:
One identifier for one vulnerability or exposure
One standardized description for each vulnerability or exposure
A dictionary rather than a database
A method for disparate databases and tools to “speak” the same language
The way to interoperability and better security coverage
A basis for evaluation among services, tools, and databases
Free for the public to download and use
Industry-endorsed via the CVE Numbering Authorities, CVE Board, and the numerous products and services that include CVE
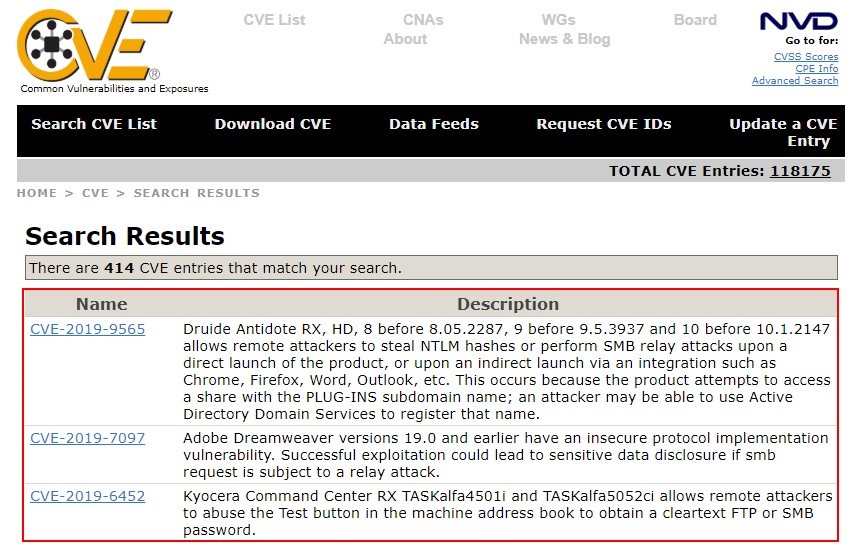
Figure 3.14: Common Vulnerabilities and Exposures (CVE)
National Vulnerability Database (NVD)
Source: https://nvd.nist.gov
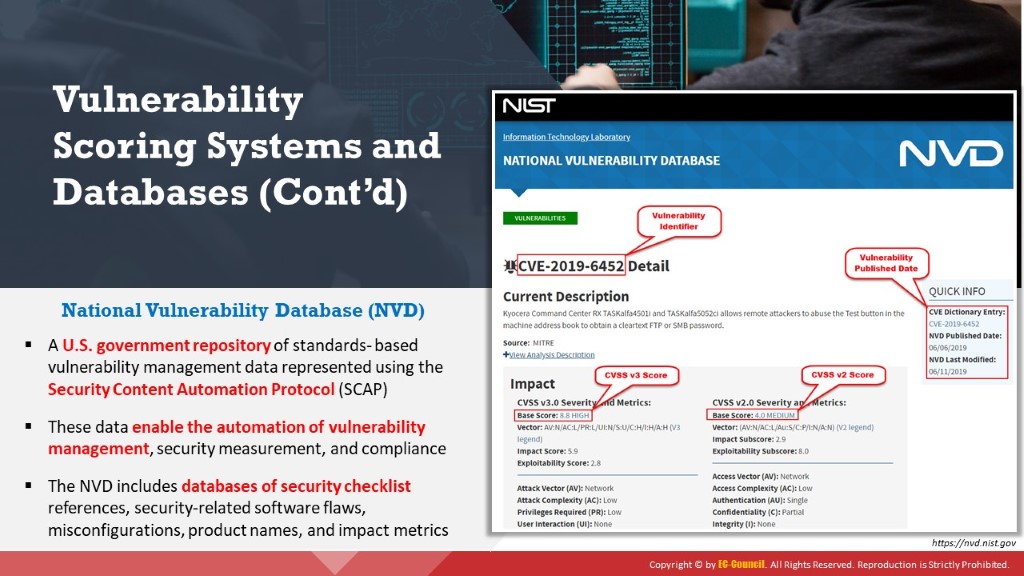
The NVD is the U.S. government repository of standards-based vulnerability management data. It uses the Security Content Automation Protocol (SCAP). Such data enable the automation of vulnerability management, security measurement, and compliance. The NVD includes databases of security checklist references, security-related software flaws, misconfigurations, product names, and impact metrics.
The NVD performs an analysis on CVEs that have been published to the CVE Dictionary. NVD staff are tasked with the analysis of CVEs by aggregating data points from the description, references supplied, and any supplemental data that are publicly available. This analysis results in association impact metrics (Common Vulnerability Scoring System – CVSS), vulnerability types (Common Weakness Enumeration — CWE), and applicability statements (Common Platform Enumeration — CPE), as well as other pertinent metadata. The NVD does not actively perform vulnerability testing; it relies on vendors, third party security researchers, and vulnerability coordinators to provide information that is used to assign these attributes.
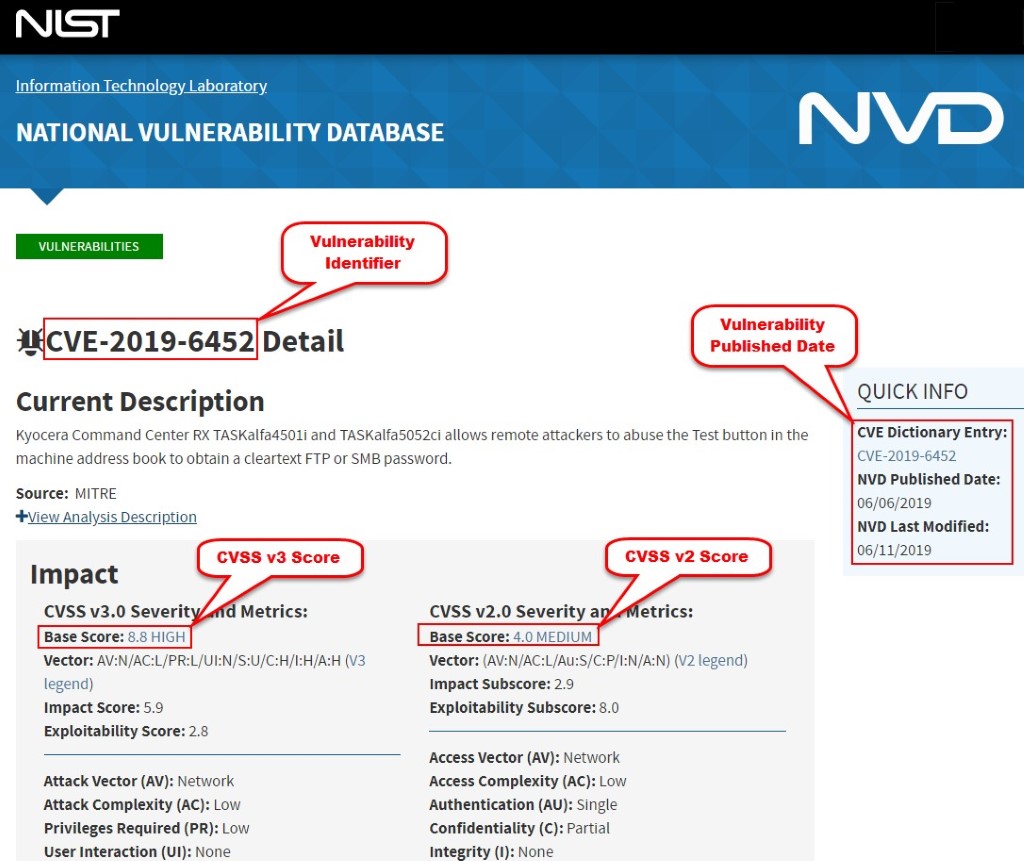
Figure 3.15: Screenshot showing CVE details in the National Vulnerability Database (NVD)
Common Weakness Enumeration (CWE)
Source: https://cwe.mitre.org
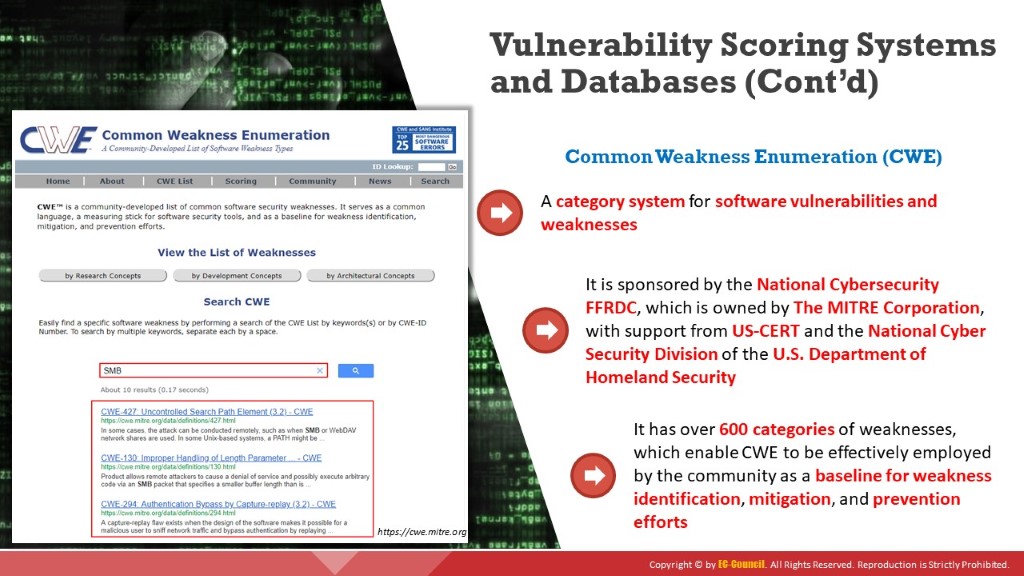
Common Weakness Enumeration (CWE) is a category system for software vulnerabilities and weaknesses. It is sponsored by the National Cybersecurity FFRDC, which is owned by The MITRE Corporation, with support from US-CERT and the National Cyber Security Division of the U.S. Department of Homeland Security. The latest version 3.2 of the CWE standard was released in January 2019. It has over 600 categories of weaknesses, which gives CWE the ability to be effectively employed by the community as a baseline for weakness identification, mitigation, and prevention efforts. It also has an advanced search technique where attackers can search and view weaknesses based on research concepts, development concepts, and architectural concepts.

Figure 3.16: Screenshot showing CWE results for SMB query