A web server is a hardware/software application that hosts websites and makes them accessible over the Internet. A web server, along with a browser, successfully implements client–server model architecture. In this model, the web server plays the role of the server, and the browser acts as the client. To host websites, a web server stores the web pages of websites and delivers a particular web page upon request. Each web server has a domain name and an IP address associated with that domain name. A web server can host more than one website. Any computer can act as a web server if it has specific server software (a web server program) installed and is connected to the Internet.
Web servers are chosen based on their capability to handle server-side programming, security characteristics, publishing, search engines, and site-building tools. Apache, Microsoft IIS, Nginx, Google, and Tomcat are some of the most widely used web server software. An attacker usually targets vulnerabilities in the software component and configuration errors to compromise web servers.
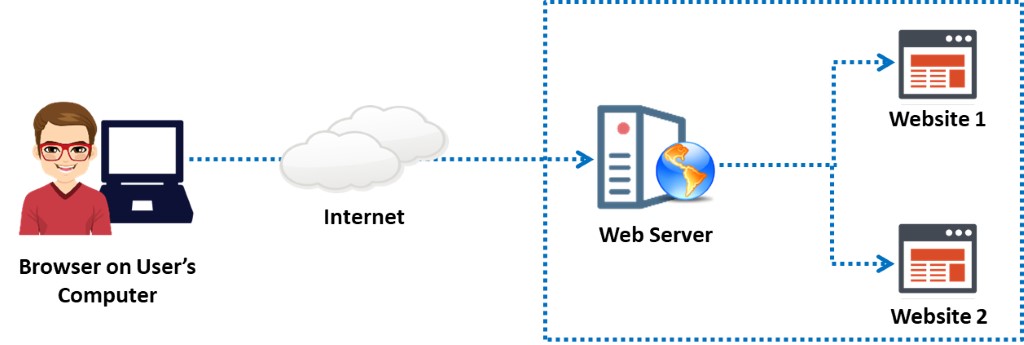
Figure 7.2: Conceptual diagram of a web server: the user visits websites hosted on a web server
Organizations can defend most network-level and OS-level attacks by adopting network security measures such as firewalls, intrusion detection systems (IDSs), and intrusion prevention systems (IPSs) and by following security standards and guidelines. This forces attackers to turn their attention to web-server- and web-application-level attacks because a web server that hosts web applications is accessible from anywhere over the Internet. This makes web servers an attractive target. Poorly configured web servers can create vulnerabilities in even the most carefully designed firewall systems. Attackers can exploit poorly configured web servers with known vulnerabilities to compromise the security of web applications. Furthermore, web servers with known vulnerabilities can harm the security of an organization. As shown in below figure, organizational security includes seven levels from stack 1 to stack 7.
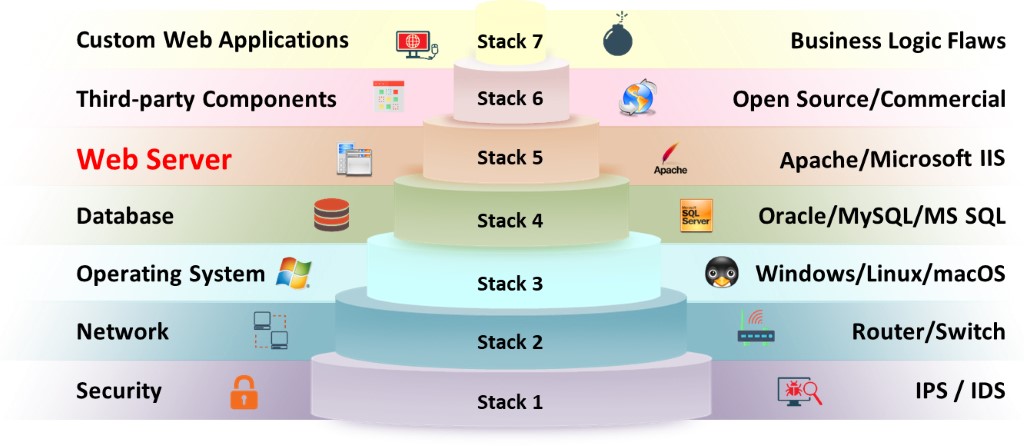
Figure 7.3: Levels of organizational security
Common Goals behind Web Server Hacking
Attackers perform web server attacks with certain goals in mind. These goals may be either technical or non-technical. For example, attackers may breach the security of a web server and steal sensitive information for financial gains or merely for the sake of curiosity.
The following are some common goals of web server attacks:
Stealing credit-card details or other sensitive credentials using phishing techniques
Integrating the server into a botnet to perform denial of service (DoS) or distributed DoS (DDoS) attacks
Compromising a database
Obtaining closed-source applications
Hiding and redirecting traffic
Escalating privileges
Some attacks are performed for personal reasons, rather than financial gains:
For pure curiosity
For completing a self-set intellectual challenge
For damaging the target organization’s reputation
Dangerous Security Flaws Affecting Web Server Security
A web server configured by poorly trained system administrators may have security vulnerabilities. Inadequate knowledge, negligence, laziness, and inattentiveness toward security can pose the greatest threats to web server security.
The following are some common oversights that make a web server vulnerable to attacks:
Failing to update the web server with the latest patches
Using the same system administrator credentials everywhere
Allowing unrestricted internal and outbound traffic
Running unhardened applications and servers
Recursive DNS query is a method of requesting DNS mapping. The query goes through DNS servers recursively until it fails to find the specified domain name to IP address mapping.
The following are the steps involved in processing recursive DNS requests; these steps are illustrated in the below figure.
Step 1:
Users who desire to resolve a domain name to its corresponding IP address send a DNS query to the primary DNS server specified in its Transmission Control Protocol (TCP)/IP properties.
Steps 2 to 7:
If the requested DNS mapping does not exist on the user’s primary DNS server, the server forwards the request to the root server. The root server forwards the request to the .com namespace, where the user can find DNS mappings. This process repeats recursively until the DNS mapping is resolved.
Step 8:
Ultimately, when the system finds the primary DNS server for the requested DNS mapping, it generates a cache for the IP address in the user’s primary DNS server.
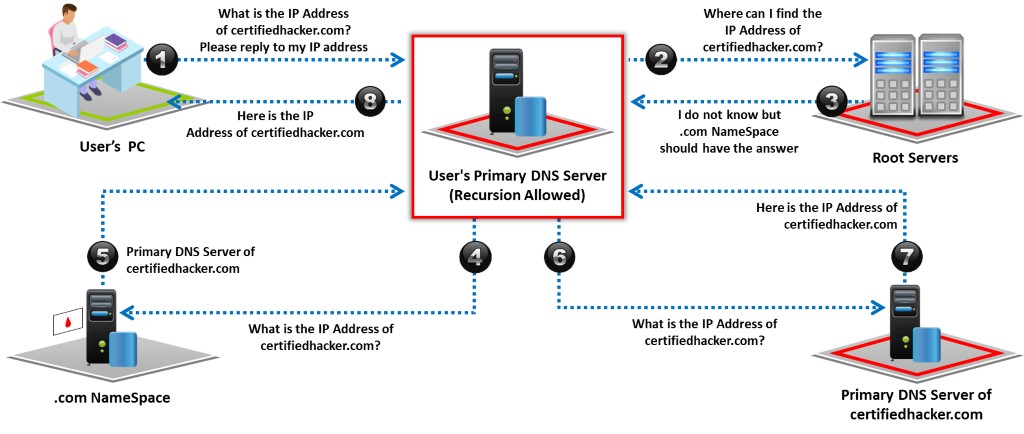
Figure 7.5: Recursive DNS query
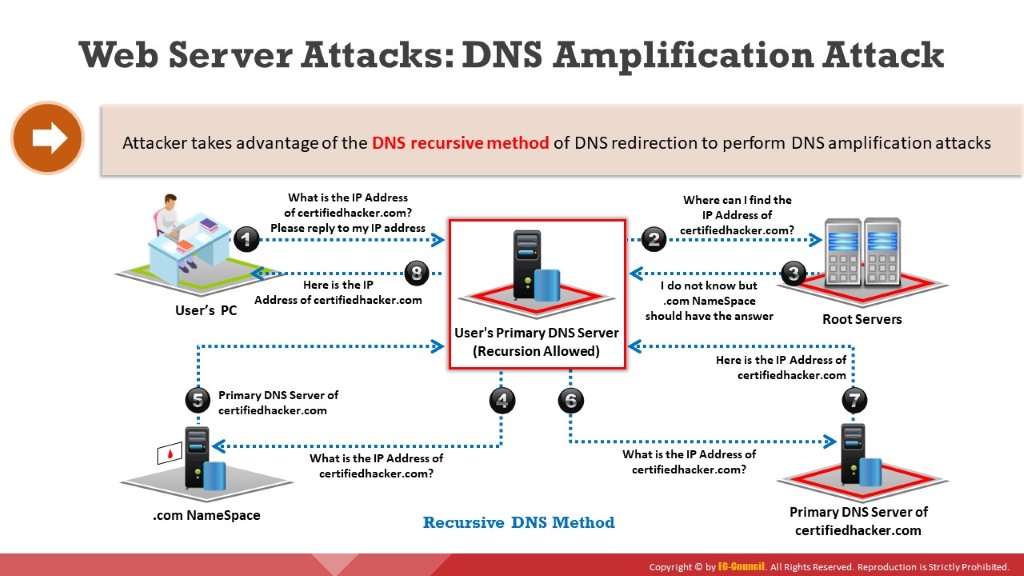
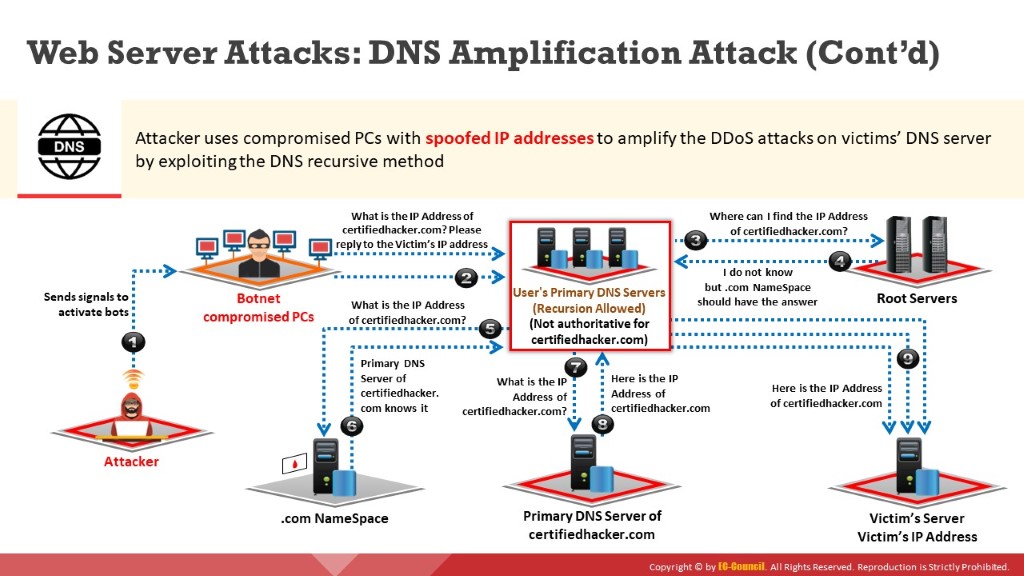
Attackers exploit recursive DNS queries to perform a DNS amplification attack that results in DDoS attacks on the victim’s DNS server.
The following are the steps involved in a DNS amplification attack; these steps are illustrated in the below figure.
Step 1:
The attacker instructs compromised hosts (bots) to make DNS queries in the network.
Step 2:
All the compromised hosts spoof the victim’s IP address and send DNS query requests to the primary DNS server configured in the victim’s TCP/IP settings.
Steps 3 to 8:
If the requested DNS mapping does not exist on the victim’s primary DNS server, the server forwards the requests to the root server. The root server forwards the request to the .com or respective top-level domain (TLD) namespaces. This process repeats recursively until the victim’s primary DNS server resolves the DNS mapping request.
Step 9:
After the primary DNS server finds the DNS mapping for the victim’s request, it sends a DNS mapping response to the victim’s IP address. This response goes to the victim because bots use the victim’s IP address. The replies to copious DNS mapping requests from the bots result in DDoS on the victim’s DNS server.
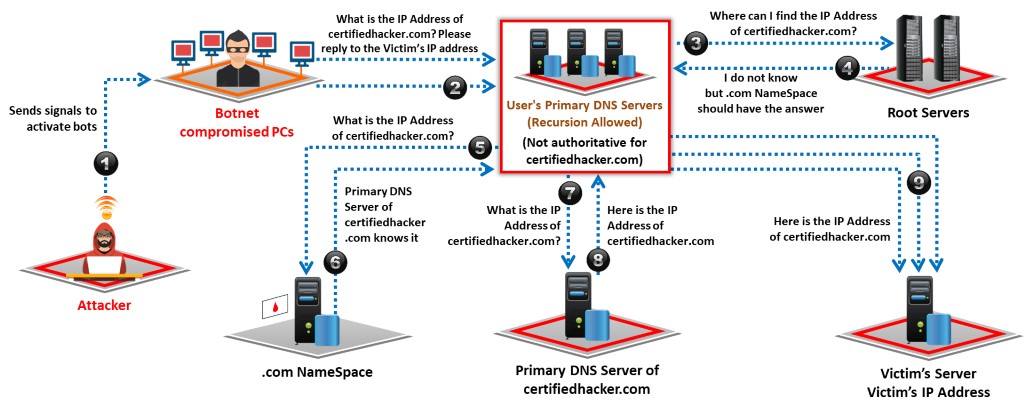
Figure 7.6: DNS amplification attack
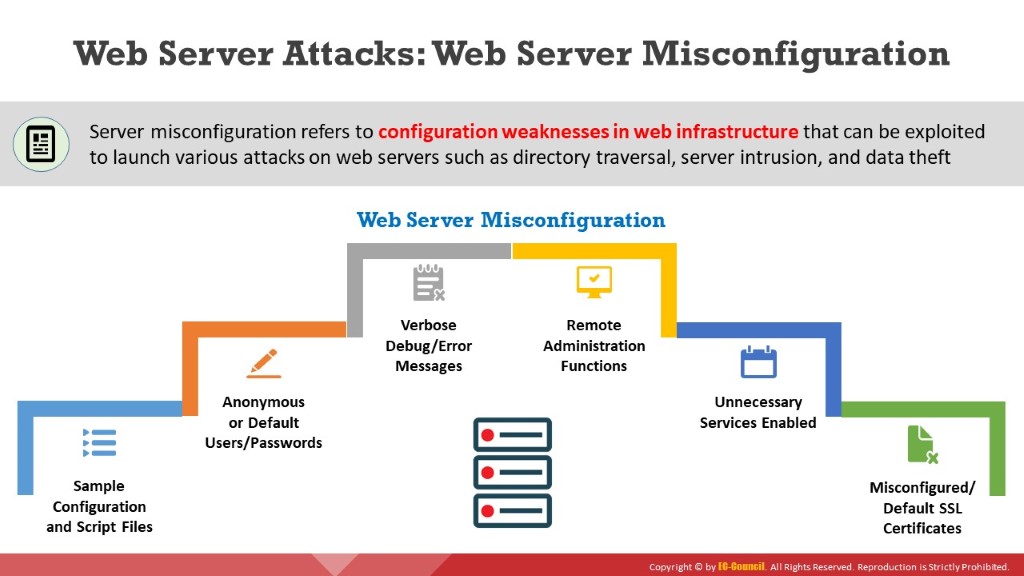
Web server misconfiguration refers to the configuration weaknesses in web infrastructure that can be exploited to launch various attacks on web servers, such as directory traversal, server intrusion, and data theft. The following are some web server misconfigurations:
Verbose debug/error messages
Anonymous or default users/passwords
Sample configuration and script files
Remote administration functions
Unnecessary services enabled
Misconfigured/default SSL certificates
An Example of a Web Server Misconfiguration
“Keeping the server configuration secure requires vigilance”—Open Web Application Security Project (OWASP)
Administrators who configure web servers improperly may leave serious loopholes in the web server, thereby providing an attacker the chance to exploit the misconfigured web server to compromise its security and obtain sensitive information. The vulnerabilities of improperly configured web servers may be related to configuration, applications, files, scripts, or web pages. An attacker searches for such vulnerable web servers to launch attacks. The misconfiguration of a web server provides the attacker a path to enter the target network of an organization. These loopholes in the server can also help an attacker bypass user authentication. Once detected, these problems can be easily exploited and may result in the total compromise of a website hosted on the target web server.
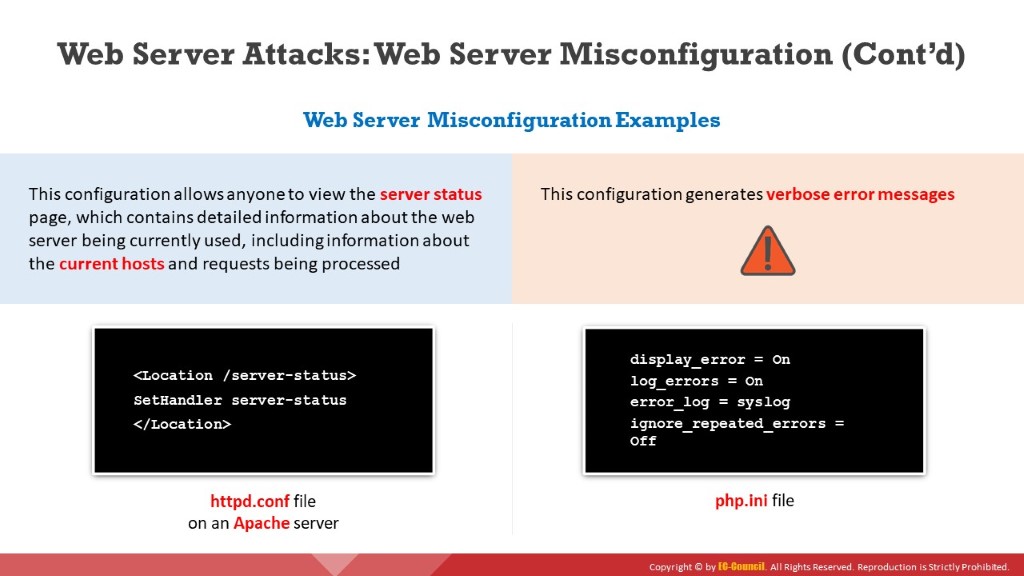
As shown in the below figure, the configuration may allow anyone to view the server status page, which contains detailed information about the current use of the web server, including information about the current hosts and requests being processed.

Figure 7.9: Screenshot displaying the httpd.conf file on an Apache server
As shown in the below figure, the configuration may give verbose error messages.
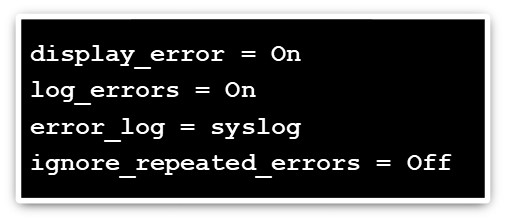
Figure 7.10: Screenshot displaying the php.ini file

An attacker attempts to exploit weaknesses to hack well-chosen passwords. The most common passwords found are password, root, administrator, admin, demo, test, guest, qwerty, pet names, and so on.
The attacker mainly targets the following through web server password cracking:
SMTP and FTP servers
Web shares
SSH tunnels
Web form authentication
Attackers use different methods such as social engineering, spoofing, phishing, a Trojan horse or virus, wiretapping, and keystroke logging to perform web server password cracking. In many hacking attempts, the attacker starts with password cracking to prove to the web server that they are a valid user.
Web Server Password Cracking Techniques
Password cracking is the most common method of gaining unauthorized access to a web server by exploiting flawed and weak authentication mechanisms. Once the password is cracked, an attacker can use the password to launch further attacks.
We present some details of various tools and techniques used by attackers to crack passwords. Attackers can use password cracking techniques to extract passwords from web servers, FTP servers, SMTP servers, and so on. They can crack passwords either manually or with automated tools such as THC Hydra, Ncrack, and RainbowCrack. The following are some techniques attackers use to crack passwords:
Guessing: This is the most common method of cracking passwords. In this method, the attacker guesses possible passwords either manually or by using automated tools provided with dictionaries. Most people tend to use their pets’ names, loved ones’ names, license plate numbers, dates of birth, or other weak passwords such as “QWERTY,” “password,” “admin,” etc. so that they can remember them easily. The attacker exploits this human behavior to crack passwords.
Dictionary attack: A dictionary attack uses a predefined file containing various combinations of words, and an automated program enters these words one at a time to check if any of them are the password. This might not be effective if the password includes special characters and symbols. If the password is a simple word, then it can be found quickly. Compared to a brute-force attack, a dictionary attack is less time-consuming.
Brute-force attack: In the brute-force method, all possible character combinations are tested; for example, the test may include combinations of uppercase characters from A to Z, numbers from 0 to 9, and lowercase characters from a to z. This method is useful for identifying one-word or two-word passwords. If a password consists of uppercase and lowercase letters as well as special characters, it might take months or years to crack the password using a brute-force attack.
Hybrid attack: A hybrid attack is more powerful than the above techniques because it uses both a dictionary attack and brute-force attack. It also uses symbols and numbers. Password cracking is easier with this method than with the above methods.
The attacker can also use automated tools such as Hashcat, THC Hydra, and Ncrack to crack web passwords and hashes.
THC Hydra
Source: https://github.com
THC Hydra is a parallelized login cracker that can attack numerous protocols. This tool is a proof-of-concept code that provides researchers and security consultants the possibility to demonstrate how easy it would be to gain unauthorized remote access to a system.
Currently, this tool supports the following protocols: Asterisk; Apple Filing Protocol (AFP); Cisco Authentication, Authorization, and Accounting (AAA); Cisco auth; Cisco enable; Concurrent Versions System (CVS); Firebird; FTP; HTTP-FORM-GET; HTTP-FORM-POST; HTTP-GET; HTTP-HEAD; HTTP-POST; HTTP-PROXY; HTTPS-FORM-GET; HTTPS-FORM-POST; HTTPS-GET; HTTPS-HEAD; HTTPS-POST; HTTP-Proxy; ICQ; Internet Message Access Protocol (IMAP); Internet Relay Chat (IRC); Lightweight Directory Access Protocol (LDAP); Memcached; MongoDB; Microsoft SQL Server; MySQL; Network Control Protocol (NCP); Network News Transfer Protocol (NNTP); Oracle Listener; Oracle system identifier (SID); Oracle; PC-Anywhere; personal computer Network File System (PC-NFS); POP3; Postgres; Radmin; Remote Desktop Protocol (RDP); Rexec; Rlogin; Rsh; Real Time Streaming Protocol (RTSP); SAP R/3; Session Initiation Protocol (SIP); Server Message Block (SMB); Simple Mail Transfer Protocol (SMTP); SMTP Enum; Simple Network Management Protocol (SNMP) v1+v2+v3; SOCKS5; SSH (v1 and v2); SSH key; Subversion; TeamSpeak (TS2); Telnet; VMware-Auth; Virtual Network Computing (VNC); and Extensible Messaging and Presence Protocol (XMPP).

Figure 7.14: Screenshot of THC Hydra password cracker